Directory traversal (or path traversal) vulnerabilities enable attackers to read arbitrary files (e.g.: application source code, credentials and other other sensitive data) on the web application server. These vulnerabilities exist when applications don't handle user-supplied input properly in the file paths. By modifying the client's request, attackers can trick the web application into accessing files outside its intended location by basically hitchhiking through directories.
Portswigger - Server-Side Request Forgery [SSRF]
Server-Side Request Forgery (SSRF) allows an attacker to cause the server-side application to make an HTTP requests to an unintended, arbitrary (internal or external) location. SSRF vulnerabilities currently hold the #10 spot on the OWASP Top 10 list (as of 2021).
Portswigger - Authentication vulnerabilities
Authentication is the process of verifying that a user is who they claim to be. Authentication vulnerabilities can allow attackers to gain access to sensitive data or functionality. They also expose additional attack surface for further exploits.
Portswigger - File Upload vulnerabilities
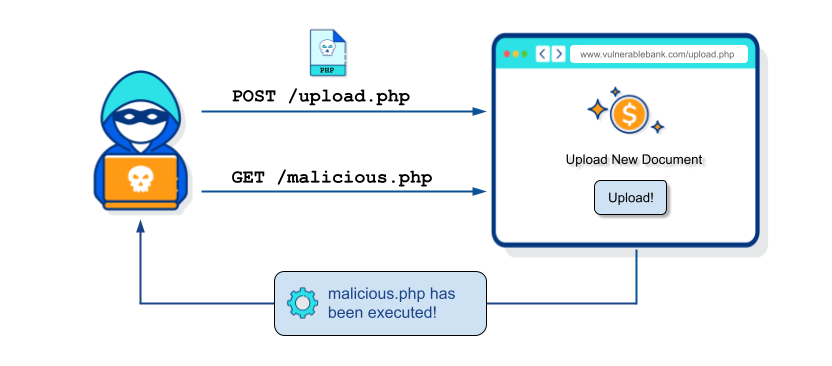
File Upload vulnerabilities occur when an attacker can upload arbitrary malicious files to a web server without proper validation. This includes insufficient checks on the file's contents, type or size. Once uploaded, these files may be executed, potentially causing havoc on the web server and on its underlying infrastructure.
Portswigger - Access control vulnerabilities
Access Control vulnerabilities allow unauthorized users to access restricted resources or perform actions beyond their permitted scope. Such failures often result in unauthorized disclosure, modification, or deletion of data. Broken Access Control vulnerabilities currently hold the #1 spot on the OWASP Top 10 list (as of 2021).



